How to Load Test SAML SSO Secured Websites with JMeter
Many websites use tokens for authenticating users in distributed SSO (single sign-on) systems. In these types of systems, service providers delegate authentication and authorization functions to other applications: identity providers (IdPs) or authentication services. In this post, we will go over implementing JMeter scripts for load testing web services that use SAML tokens for client authentication and security.
Token Interactions and Authentications
Token interactions include three principal parties: the Client or user, the IdP (identity provider), and the SP (Service Provider) or application. There can be multiple SPs and IdPs in one system. The entire process can be described in three steps:
The Identity Provider authenticates the Client in a specified way: login/password, access key, certificate, etc.
The Client requests the Identity Provider to provide a token for a certain application (Service Provider). The Identity Provider generates the token and sends it to the client.
The Client is authenticated in the application (Service Provider) with this token.
Applications (SPs) that communicate with social networks, usually Facebook, to authorize users, are a common example of authentication via IdP. In these cases, the application delegates the authentication of its users to the social network, which operates as an authentication service. Then, the IdP provides the information about the logged user in the form of a token аnd the service providers (SPs) or the application that requested the authorization uses this token for authorization, authentication, and identification of the logged user.
This process is specific for active clients on mobile or desktop. For passive clients, like web browsers, the authentication comes with an automatic redirect between the identity provider and the service provider. There are a few standards that define interactions between the clients, the IdP and the SP, and define the token format. OAuth, OpenID, and SAML are among them.
SAML (Security Assertion Markup Language) Authentication
SAML, Security Assertion Markup Language, defines interoperability and protocol between the identity provider and the service provider for exchanging authentication and authorization data by the means of tokens.
The basic building blocks of the standard are:
Assertions: XML format of SAML tokens.
Protocols: Supported messages between standard parties.
Bindings: A mechanism of exchanging messages over the transport protocols.
Profiles: A set of assertions, protocols, and bindings in the typical use case of standard application. Web Browser SSO is one of these profiles.
How to Run a JMeter Test on a SAML Website
There are two alternative flows for SAML SSO: The flow initiated by the service provider and the flow initiated by the identity provider. In this example, we will go over a flow initiated by the service provider. The full test build can be seen in this image:
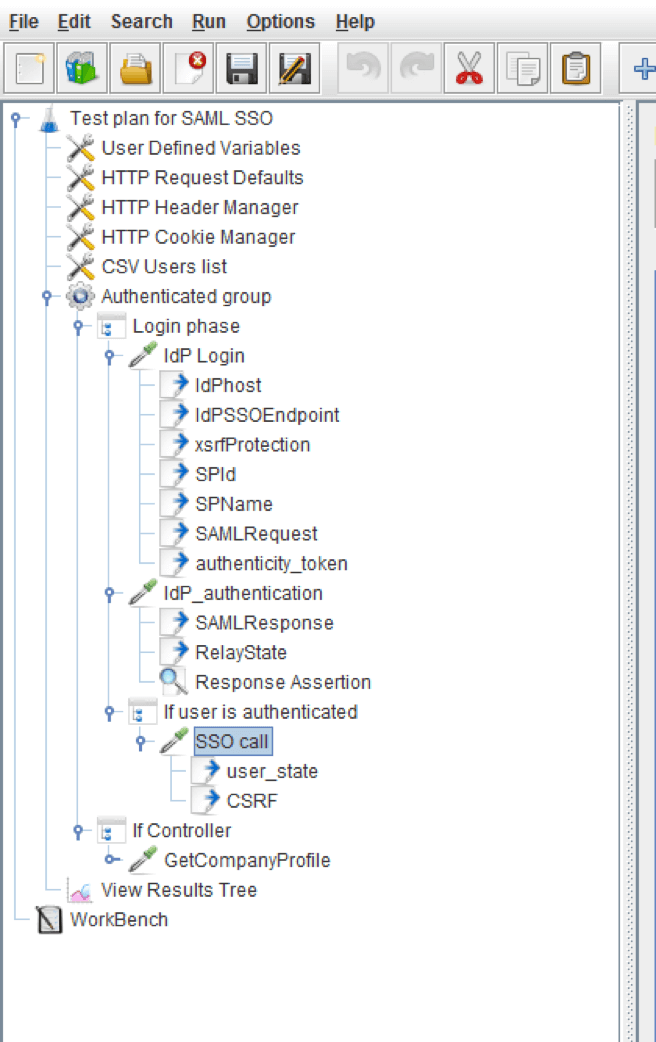
Now let’s break it down.
Step 1: The User Attempts to Access the Service Provider’s Protected Resource
As the user has not been authenticated, the SP redirects the user to the identity provider URL, to create a token. This identity provider URL is added by the SP from the SAML configuration. While redirecting, the application adds the SAMLRequest parameter to the query string. The IdP returns the HTML page, which has all required parameters to continue authentication. This is the step the user is usually presented with the login screen to enter user credentials (if the user is authenticated via login and password) on the browser.
Using the JMeterRegular Expression Extractor, it's possible to extract the SAMLRequest, authentication token, IDP host, end-point, and other parameters from the HTML page to use them in the authentication request. To do this, just add child Regular Expression Extractor Post Processors to the HTTP sampler that performs login action.
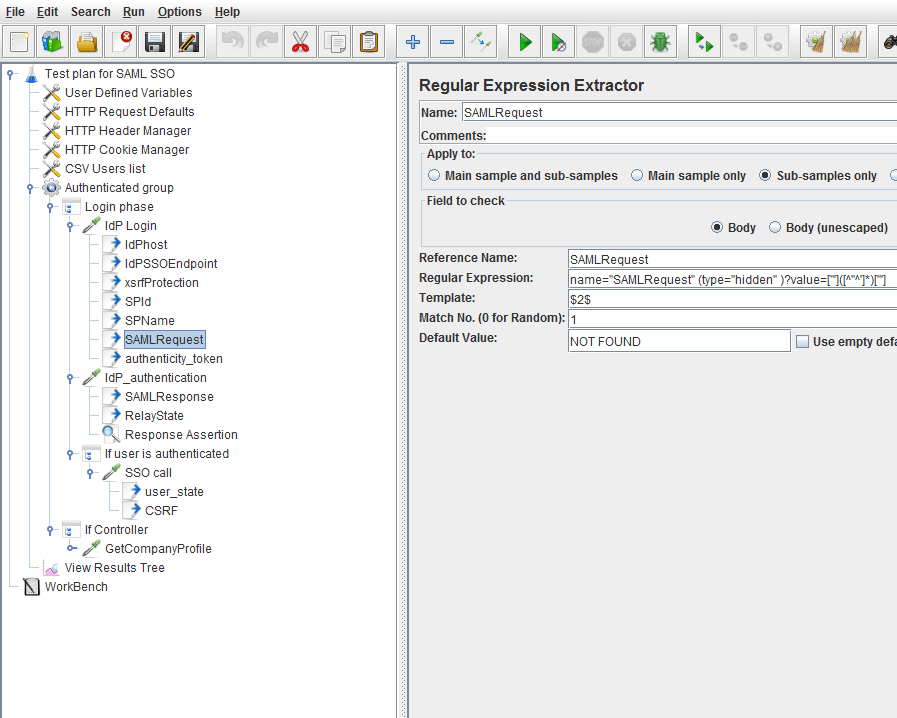
The selected Regular Expression Extractor Post Processor extracts the SAMLRequest string:
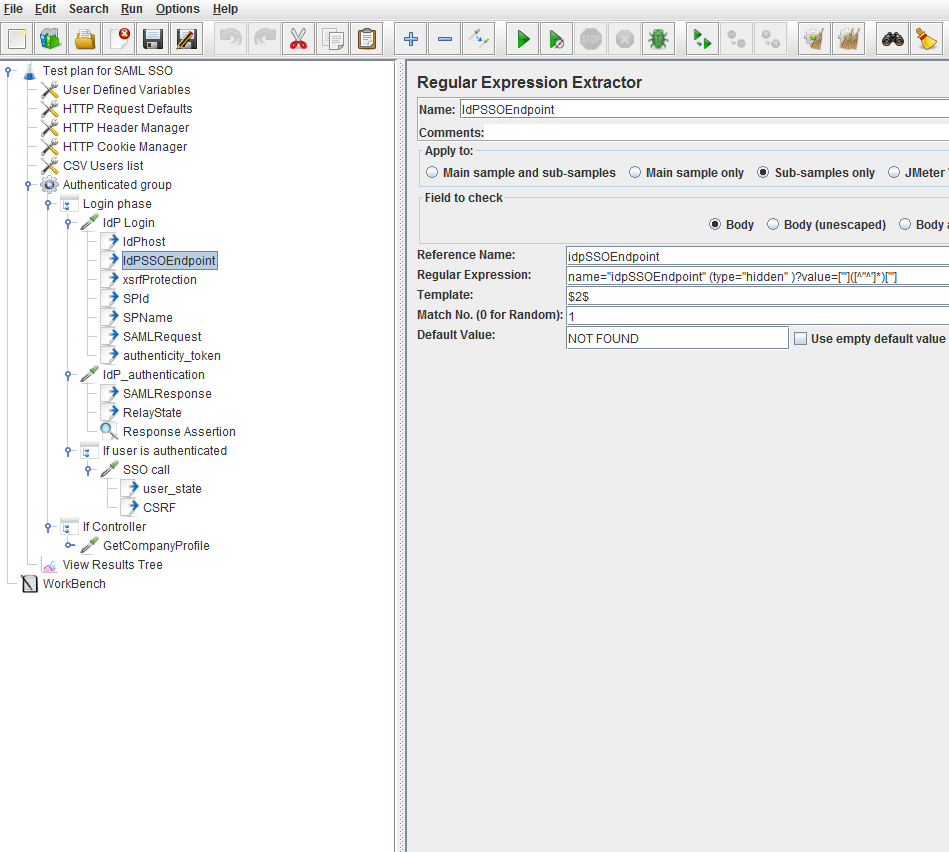
This selected regular expression extractor post processor extracts the IdP endpoint string:
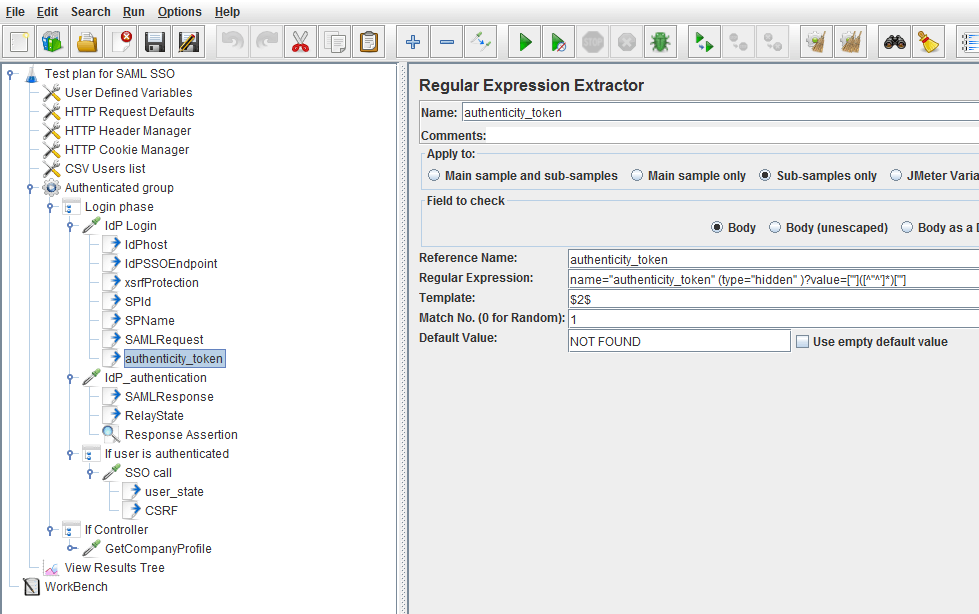
This selected Regular Expression Extractor Post Processor extracts the authenticity token string:
 In the same way, other parameters that are required to implement the script can be extracted from the HTML response.
In the same way, other parameters that are required to implement the script can be extracted from the HTML response.
Step 2: The Authentication Request Is Composed and Sent to the IdP
The extracted parameters are used to execute the next HTTP sampler to perform IdP authentication, for example: to be passed to the parameters section of the HTTP sampler.
If the data provided to the IdP is correct, the IdP authenticates the user and returns an HTML page with the SAMLResponse, RelayState, and other parameters. The SAMLResponse contains assertions that are signed and encoded by the IdP.
By using the JMeter Regular Expression Extractor, these parameters are extracted from HTML and used in the next HTTP request. To do this, just add child Regular Expression Extractor Post Processors to the HTTP sampler that performs IdP authentication.
This selected Regular Expression Extractor Post Processor extracts the SAMLResponse string:
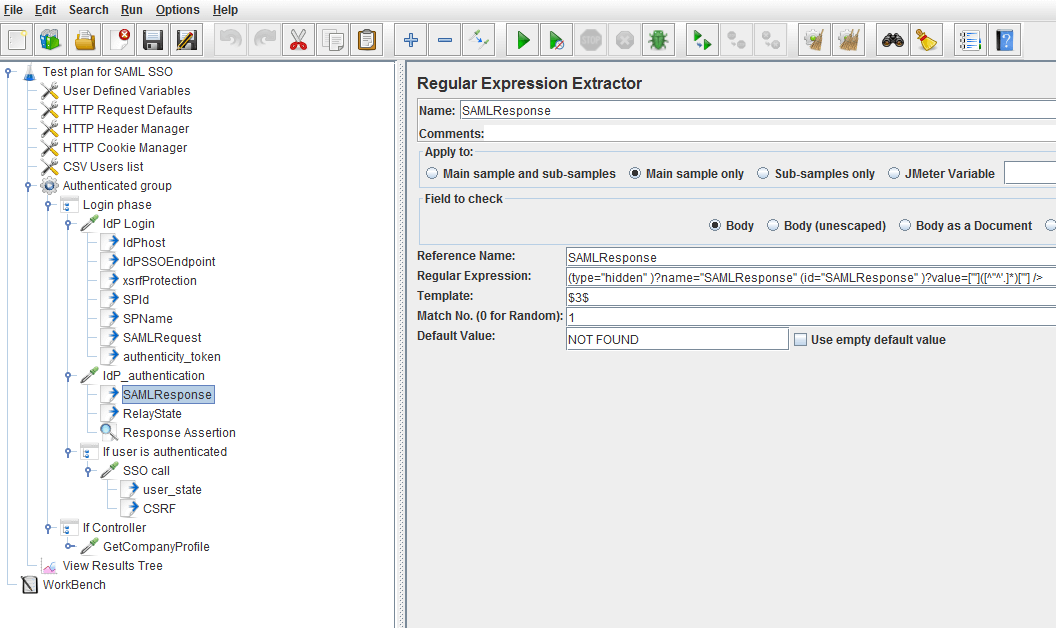
This selected Regular Expression Extractor Post Processor extracts the RelayState string:
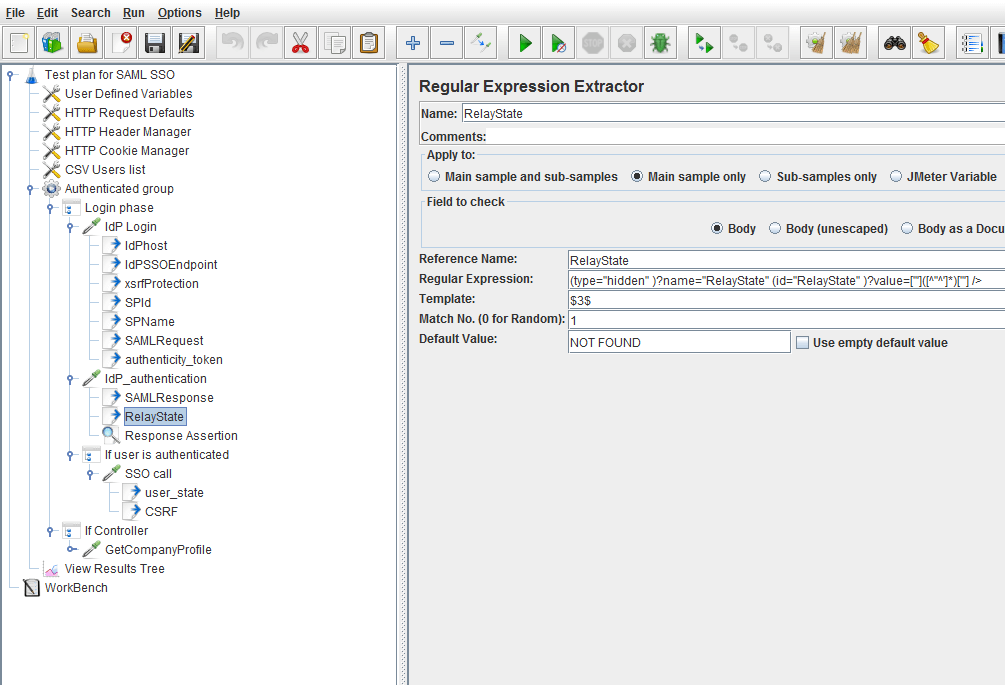
The Response Assertion child element verifies that the user is authenticated. Upon the assertion result, other samplers are called. In this particular case, the Response Assertion tests for the string pattern “You have now been authenticated”.
Step 3: The Client Sends the Request to the Application and Passes the RelayState and SAMLResponse as Parameters
The SSO call HTTP sampler implements this step. This sampler is called if the assertion of the previous HTTP sampler has been passed, and it means the IdP authenticated the user. In this script, the SAMLResponse and RelayState extracted parameters are passed in the parameters section of the SSO call HTTP sampler.
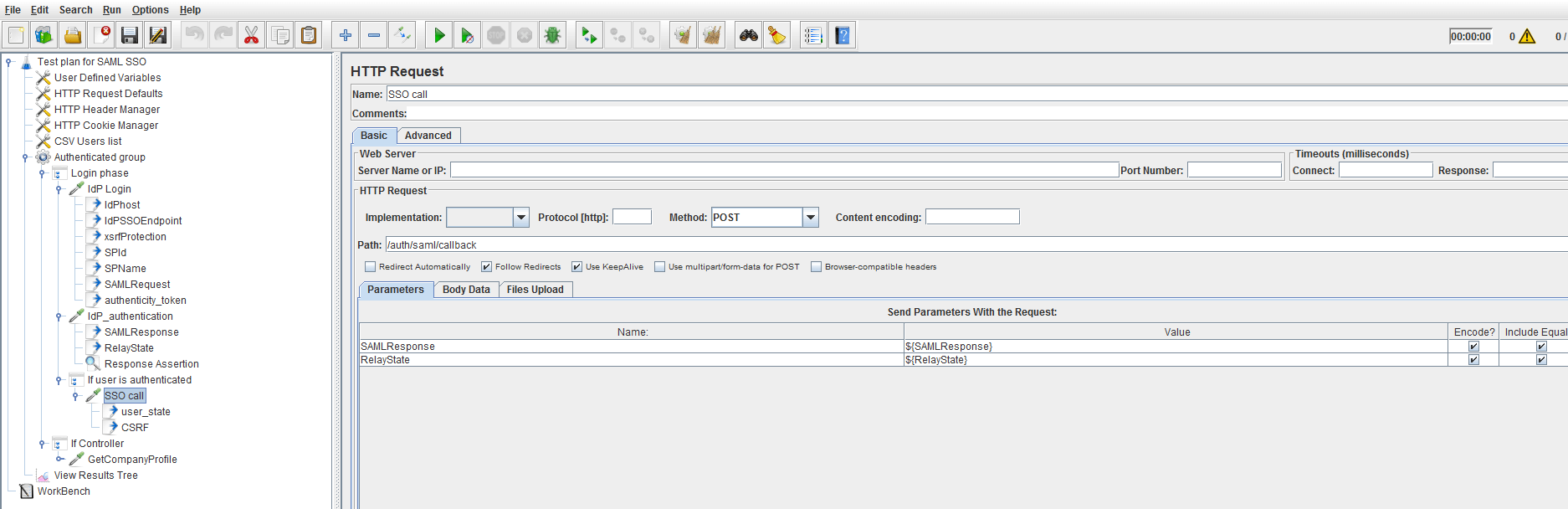
The application then checks the signatures of the SAMLResponse and each of the assertions inside of it, creates a user session and sets a cookie with the user session ID. Don't forget to include the HTTP Cookie manager configuration element to your script. Further on, after the authentication section of the script has been implemented, it's possible to include other samples that perform designed use-cases scenarios, so as to conduct load tests of the application.
Congratulations! You can now build and run performance testing scenarios for websites secured with SAML SSO.

