Safeguard Your Xamarin Apps From Threats With Dotfuscator
To do this, we will use PreEmptive Protection – Dotfuscator, an obfuscator, and protection tool that now also supports Xamarin. You will, of course, need your app to be developed using Visual Studio 2017 for Windows.
Protection from Cyber Threats is Worthwhile
There are many people who do not realize how much danger they are in when it comes to outside cyber threats. They are worried that there are larger forces in action that may cause them to lose some of the precious data that they have worked so hard to build up, and they are not wrong about this.
If you have apps created with Xamarin, you need to protect them with Dotfuscator. There is simply no excuse not to keep your information under a tight lock and key these days, and you are strongly encouraged to act rapidly so you don’t end up in a situation where you are unable to access the precious data that you know you need to keep safe. Too many people have allowed the data out into the wild, and you simply CANNOT follow in those footsteps.

Step 1: Install and Set Up Dotfuscator
You will need to set up Dotfuscator on your machine, register your copy, and record the path to the command line interface.
Here’s how to set it up:
Use the PreEmptive Solutions website and navigate to the Dotfuscator Downloads page.
From here download the latest release of Dotfuscator Community Edition (CE) for Visual Studio 2017.
Now run the VSIX file that you have downloaded and follow the set-up instructions.
Next launch Visual Studio 2017 and go to Tools – PreEmptive Protection – Dotfuscator to start the Dotfuscator CE user interface. As explained earlier, your copy of Dotfuscator must be registered before you can use it. You will be prompted by Dotfuscator to log in when you use it for the first time. You will need to register your copy of Dotfuscator before you can use the command line interface. Dotfuscator will ask you to register when you run it for the first time; follow these instructions.
If you want to register later or find out your registration status, check the registration status text in the upper-right corner of the Dotfuscator webpage.
The path to CLI is required to configure the build integration. You can find this path by navigating to the install directory for your installation of Visual Studio 2017. For example, the default install directory for Visual Studio 2017 Professional is:
C:\Program Files (x86)\Microsoft Visual Studio\2017\Professional. Inside this directory, find the Dotfuscator Community Edition extension files in*\Common7\IDE\Extensions\PreEmptiveSolutions\DotfuscatorCE. The dotfuscatorCLI.exe executable is the Dotfuscator Community Edition command line interface. Secure the absolute path to the executable for later use.
Step 2: Download the Build Integration File
The Dotfuscator team has created an MSBuild targets file to aid the integration process. This data can be referenced by your Xamarin projects. Download this here.
Now save the PreEmptive.Dotfuscator.Xamarin.Targets file to your application’s solution directory, adding it to your local source control.
Step 3: Editing the Project for Build Integration
To modify your project file for the Visual Studio project that you want to obfuscate:
First, note the project build configurations that you want to guard. These are everything except Debug configurations. If you want more guidance on this, you can refer to the ‘Select What to Protect’ section of the documentation.
Using a text editor, open your project file. For instance, a project file for C# would be `YourProjectName.csproj.'
Make a note of the relative path from this file to the build integration file you have downloaded.
Next, import the build integration file by adding the following command to the file, just before the </Project> tag: <Import Project="..\..\PreEmptive.Dotfuscator.Xamarin.targets" />. This will substitute the relative path that you had noted earlier, substituting the relative path noted in Step 3.
Within the <PropertyGroup> tag and no Condition attribute, add the following tags:<DotfuscatorXamarinCliPath>C:\pathto\dotfuscatorCLI.exe</DotfuscatorXamarinCliPath>,replacing the absolute path to the Dotfuscator Community Edition CLI you had noted earlier:<DotfuscatorXamarinConfigFileName>DotfuscatorConfig.xml</DotfuscatorXamarinConfigFileName> and <DotfuscatorXamarinGenerateNewConfigFile>true</DotfuscatorXamarinGenerateNewConfigFile>.
Similarly, for each build configuration noted previously, find the related <PropertyGroup> and add the following tag: <DotfuscatorXamarinEnabled>true</DotfuscatorXamarinEnabled>
Once the last of the <ItemGroup> tags are added, add the following:<ItemGroup><None Include="DotfuscatorConfig.xml" /></ItemGroup>. Save your changes to the file and close it.
Step 4: Build the App
Finally, you can start building the app with Dotfuscator protection:
Launch your project using Visual Studio 2017.
Now choose the solution build configuration that exercises a project build configuration you want to protect.
Build your project. Post the first build, ensure that the output shows the following lines regarding the Dotfuscator.
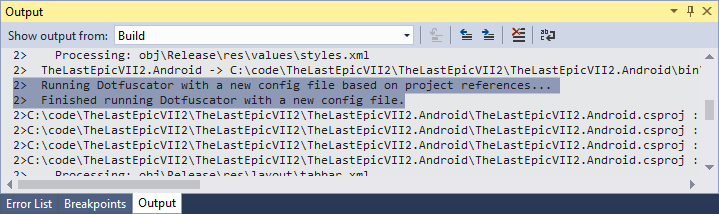
You will find the addition of a DotfuscatorConfig.XML file in your project. This data is the Dotfuscator config file, and it tells the program how to obfuscate the code. The recommended use is to check it into your source control.
You will also see the new DotfuscatorReports directory in your project directory. This list contains the information about project obfuscation process including the details on reversing the process, and this information should be treated like build output and have the source control ignore it.
Now you need to test the app, and if there are errors, further Dotfuscator configuration may be required to correct these mistakes.
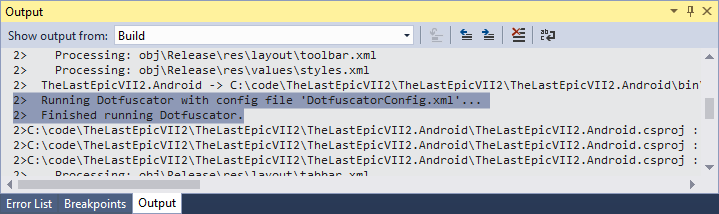
You can continue developing and building your app per usual. Whenever Dotfuscator is called in the build, the output will display the following:
Summary
This post explains the benefits and procedures of obfuscating your apps using Dotfuscator. You can protect your Android, iOS, and UWP apps utilizing the process described here. If you need more information on protecting your Xamarin projects with the help of a Dotfuscator, visit the Xamarin Dotfuscator User Guide. If you have any other queries or comments, please use the feedback section below.

