AppOps with Kubernetes and Devtron - The Perfect Fit
Kubernetes needs no introduction in this cloud-native world. It was born when I was a middle-aged man. Years later, I am still as young as earlier (take with a pinch of salt) while Kubernetes grew out to be a fine tool that outperformed other platforms in enabling operational efficiency and application resilience.
In the past, I wrote several articles and guides on Kubernetes and supported platforms. But then, in the pursuit of appyness, there is no end to innovation.
In this article today, I take up another interesting use-case of Devtron as an open-source platform that refactors the Kubernetes ecosystem into an easy-to-use AppOps model.
First, a few basics.
What Are We Trying to Achieve?
Exploring the Devtron platform to validate its capabilities to build, deploy and manage apps on a K8s cluster.
What is Devtron?
Devtron is an open-source, GUI based platform to deploy and manage Kubernetes applications. The platform allows you to manage an entire application ecosystem through a single control pane that spans across multiple cloud service providers with varying environments. While doing so, efficient collaboration and security sits at its core to naturally enable a DevOps model.
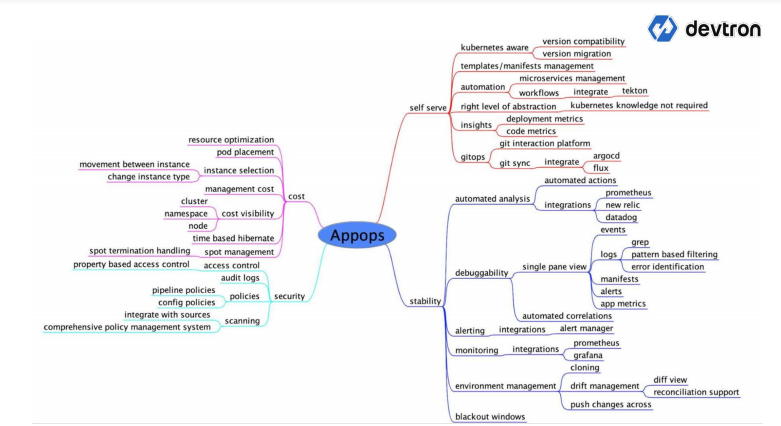
Let's get a hands on.
Stage 1: Creating an Amazon EKS Cluster
We will start with configuring an AWS EKS cluster (you may also use a GKE or AKS cluster as per your choice). In case you already have a cluster setup, you may skip over to Stage 2.
Part One: Installing the AWS CLI
To work with AWS on the command line, you need to install the AWS CLI, that enables the creation and management of AWS services from a Linux, macOS, or Windows console. If you’re logged into the AWS console, you can spin up the AWS CloudShell, which comes preinstalled with the AWS CLI.
To install AWS CLI on Linux, log into your Linux operating system and access the console.
- Fetch the latest AWS CLI version for Linux-x86(64-bit) platform.
$ curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"$ unzip awscliv2.zip$ sudo ./aws/install$ aws --versioneksctl command-line tool on the Linux operating system. Note that this is also possible on macOS and Windows. The following commands will cover how to install the tool on 64-bit Linux.
- Fetch the latest version of
eksctl.
$ curl --silent --location "https://github.com/weaveworks/eksctl/releases/latest/download/eksctl_$(uname -s)_amd64.tar.gz" | tar xz -C /tmp/usr/local/bin.
$ sudo mv /tmp/eksctl /usr/local/bineksctl version. In my case, it was 0.40.0 and might be different for you.
$ eksctl version
0.40.0- The next step is to deploy an Amazon EKS cluster. To do so, use the
create clustercommand, that sets up all the required resources.
$ eksctl create cluster \
--name devtron-darwin-cluster \
--region us-east-2 \
--nodegroup-name devtron-darwin-nodegroup \
--node-type t2.micro \
--nodes 4 \
--nodes-min 1 \
--nodes-max 5 \
--managed- a given name,
- region,
- nodegroup-name,
- node-type, nodes,
- minimum nodes and maximum nodes of the node group,
- and then deploys the cluster on a managed node group type.
kubectl,an open-source command-line tool used to interact with Kubernetes clusters.
- Fetch the
kubectltool for Kubernetes version 1.18. Note that there are different links available for lower or higher versions, however, to use Devtron, version 1.18 or above is recommended.
$ curl -o kubectl https://amazon-eks.s3.us-west-2.amazonaws.com/1.18.9/2020-11-02/bin/linux/amd64/kubectlkubectl binary fetched.
$ chmod +x ./kubectl$ mkdir -p $HOME/bin && cp ./kubectl $HOME/bin/kubectl && export PATH=$PATH:$HOME/binkubectl installed to confirm the installation has been successful and as intended.
$ kubectl version --short --client
Client Version: v1.18.9-eks-d1db3c
$ kubectl get service
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.100.0.1 <none> 443/TCP 33dStage 2: Installing Devtron
kubectl, Helm 2, or Helm 3.
- Start by changing the Kubernetes context to the EKS cluster that you want to use, change the region and cluster name values to those specific to your environment.
$ aws eks --region us-east-2 update-kubeconfig --name darwin-devtron-cluster02namespace to use for Devtron using devtroncd as the name.
$ kubectl create namespace devtroncd$ curl -fsSL -o get_helm.sh https://raw.githubusercontent.com/helm/helm/master/scripts/get-helm-3$ chmod 700 get_helm.sh$ ./get_helm.shyum package manager to install OpenSSL.
$ sudo yum -y install openssl$ helm version
WARNING: Kubernetes configuration file is group-readable. This is insecure. Location: /home/cloudshell-user/.kube/config
WARNING: Kubernetes configuration file is world-readable. This is insecure. Location: /home/cloudshell-user/.kube/config
version.BuildInfo{Version:"v3.5.3", GitCommit:"041ce5a2c17a58be0fcd5f5e16fb3e7e95fea622", GitTreeState:"dirty",GoVersion:"go1.15.8"}$ helm repo add devtron https://helm.devtron.ai$ helm install devtron devtron/devtron-operator --namespace devtroncd --set secrets.POSTGRESQL_PASSWORD=new-password-heredevtroncd namespace and take note of the pod that begins with inception-849d647c4d.
$ kubectl get pod -n devtroncd$ kubectl logs -f inception-849d647c4d-ldncs -n devtroncd$ kubectl -n devtroncd get installers installer-devtron -o jsonpath='{.status.sync.status}'
Applied[cloudshell-user@ip-10-0-XX-XX ~]$devtroncd namespace by typing the command shown below.
$ kubectl get pods -n devtroncddevtroncd namespace.
$ kubectl -n devtroncd get secret devtron-secret -o jsonpath='{.data.ACD_PASSWORD}' | base64 -d
argocd-server-59XXXXX-XXXX[cloudshell-user@ip-10-0-XX-XX ~]$devtroncd namespace and choose the load balancer service, which has a public address that you can paste into your browser.
xxxxxxxxxx
$ kubectl get svc -n devtroncd
devtron-grafana ClusterIP 10.100.159.169
devtron-kubernetes-external-secrets ClusterIP 10.100.171.60
devtron-minio ClusterIP 10.100.230.236
devtron-minio-svc ClusterIP None
devtron-nats ClusterIP 10.100.195.145
devtron-nats-mgmt ClusterIP None
devtron-service LoadBalancer 10.100.204.202 a4777dd57858a4dc59afb0a4517b1748-XXXXXXXXXX.us-east-2.elb.amazonaws.com
PS: Dashboard URL above is edited for security purposes.
$ kubectl -n devtroncd get secret devtron-secret -o jsonpath='{.data.ACD_PASSWORD}' | base64 -d- In the Devtron dashboard, click on the Global Configurations button at the bottom left and select the option Host URL.
- To add a GitOps account, click on the GitOps tab on the left of your global configurations screen and add the Github organization and access credentials.
- Add the Git Host, the Github organization name, Git access credentials, and then click Save.
- Click on add git account, Name to your Git provider, set the URL, Authentication type, the Git Username, Password, and then click Save.
- Click Add docker registry, set the Registry name, the Registry type (in our case its ECR), add the Registry URL, the AWS region, the Amazon IAM role access Id, Secret access key, and then click Save.
- On the Devtron dashboard, click on the Applications tab; this will bring up a display with a button Add New App at the top right of the screen, click on the button.
- To enable Continuous Integration, we need to add a new workflow to our application. Click add a New Workflow, give the workflow a Name and click Save.
- Select the Trigger tab to view your available workflows. Click Select Image on the deploy step to trigger the deployment using the deployment strategy that we defined, and the pipeline will display as Progressing.
- If an earlier Installation of Devtron failed on the cluster, you might receive errors in case you try to re-install Devtron. Make sure to look at the errors that are being thrown from the
inceptionpod. You can quickly check the logs using the command below.
$ kubectl logs -f inception-d95bc9478-7blw6 -n devtroncdinception pod to that of your environment. The command below also produces similar output on any cluster.
$ pod=$(kubectl -n devtroncd get po -l app=inception -o jsonpath='{.items[0].metadata.name}')&& kubectl -n devtroncd logs -f $pod$ cd devtron-installation-script/
$ kubectl delete -n devtroncd -f yamls/
$ kubectl delete -n devtroncd -f charts/devtron/templates/devtron-installer.yaml
$ kubectl delete -n devtroncd -f charts/devtron/templates/install.yaml
$ kubectl delete -n devtroncd -f charts/devtron/crds
$ kubectl delete ns devtroncd$ cd devtron-installation-script/
$ kubectl delete -n devtroncd -f yamls/
$ kubectl -n devtroncd patch installer installer-devtron --type json -p '[{"op": "remove", "path": "/status"}]'1. To resolve the issue, run the commands below to upgrade your Devtron installation.
$ helm repo update
$ helm upgrade devtron devtron/devtron-operator -n devtroncd$ kubectl -n devtroncd get installers installer-devtron -o jsonpath='{.status.sync.status}'git-sensor pod that runs all the Git operations.
$ kubectl logs -f git-sensor-0 -n devtroncd
