How to Get Started With Istio in Kubernetes in 5 Steps
Applications nowadays are distributed as microservices all over the cloud. Organizations use Kubernetes to manage these applications at scale, which has brought great flexibility and agility for development teams.
However, microservices and multicloud applications have given rise to new challenges. Now, it is harder to configure communication between distributed services and secure the data in transit. So it is inevitable for organizations to use service mesh, specifically Istio. In this article, we will briefly look at what Istio is and then see how to install Istio in Kubernetes in just 5 steps.
What Is Istio Service Mesh?
Istio is a popular open-source service mesh implementation platform, which simplifies and secures communication between microservices in the cloud. Istio abstracts the network and security layer from the application and applies them from an infrastructure layer. It provides some major benefits, such as traffic management, security, and observability, for better control and visibility into the traffic flow between microservices.
Istio has two major components: a control plane and a data plane (refer to Fig. A below). The data plane comprises a network of L4 and L7 proxies called Envoy, which intercepts and facilitates communication between services. Envoy proxy is injected as a sidecar to each application deployed in the mesh. The control plane acts as a centralized layer to manage and configure these data plane proxies.
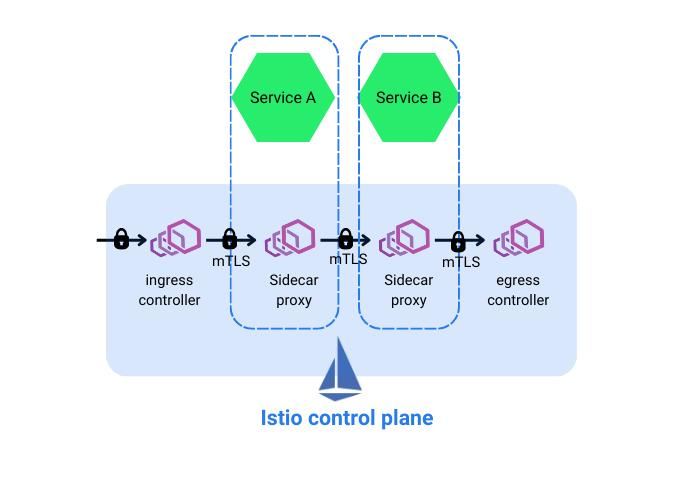
Now, let us see the prerequisites for deploying Istio in Kubernetes.
Prerequisites
- Kubernetes cluster v1.23 or later. The version used for implementation: v1.26.0.
- Download Istio in a folder.
You can download the latest Istio version by going to this path based on your OS: https://github.com/istio/istio/releases/. For this demo, I have downloaded Istio 1.17.1 for Windows.
Once you download the zip file, extract it, and you will see the following files in Istio 1.17.1 folder:
After successfully extracting Istio files, open CMD and change the directory into the folder where the Istio files are extracted to install it.
Note: Ensure <extracted Istio files root folder>/bin is in the terminal path environment variable.
Watch the Demo on How to Install Istio in 10 Minutes
If you prefer watching a demo rather than reading through this article, click on the below video to learn how to install Istio in 10 minutes:
Steps to Install Istio Service Mesh, Ingress Gateway, and Kiali Dashboard
We will follow the 5 steps outlined below to complete this tutorial.
Step 1: Deploy Istio to Kubernetes
Run the following command to deploy Istio to K8s with the demo profile:
istioctl install –set profile=demo -yIt will install Istio core, Istiod, and Ingress and Egress gateways.
Step 2: Label Namespace to Onboard Istio
For Istio to inject sidecars, we need to label a particular namespace. Once a namespace is onboarded (or labeled) for Istio to manage, Istio will automatically inject the sidecar proxy (Envoy) to any application pods deployed into that namespace.
Use the below command to label the default namespace with the Istio injection enabled tag:
kubectl label namespace default istio-injection=enablednamespace/default labeled if the tag was successful.
For now, there are no pods in the default namespace. Let us deploy a demo application to see the automatic sidecar injection in action.
Step 3: Deploy the Demo Application (Bookinfo)
Istio provides a demo application named Bookinfo, which has a few services, their corresponding service accounts, and deployments.
Now run the following command to deploy bookinfo.yaml:
kubectl apply -f samples\bookinfo\platform\kube\bookinfo.yamlYou will see the following pods being deployed in the cluster when you run kubectl get pods
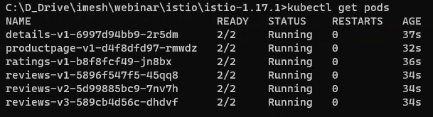
Note: Now 2 containers are running inside the pods (see 2/2 under READY). One is the application itself; the other is an Envoy proxy automatically injected into the pod by Istio.
You can also see all the services deployed by running kubectl get service
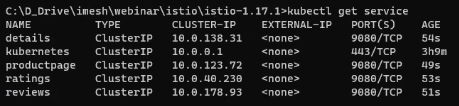
By default, the applications that are deployed in the cluster cannot be accessed externally or from outside the cluster. For that, we will have to expose the application by deploying the ingress gateway.
Step 4: Deploy the Ingress Gateway and Access the Application from Outside the Cluster
In the demo application Bookinfo, you will find an existing Istio ingress-gateway called bookinfo-gateway.yaml (manifest below).
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: gateway
annotations:
kubernetes.io/ingress.class: “istio”
spec:
rules:
– http:
paths:
– path: /productpage
pathType: Exact
backend:
service:
name: productpage
port:
number: 9080
– path: /static/
pathType: Prefix
backend:
service:
name: productpage
port:
number: 9080
– path: /login
pathType: Exact
backend:
service:
name: productpage
port:
number: 9080
– path: /logout
pathType: Exact
backend:
service:
name: productpage
port:
number: 9080
– path: /api/v1/products
pathType: Prefix
backend:
service:
name: productpage
port:
number: 9080Run the following command to deploy ingress gateway:
kubectl apply -f samples\bookinfo\networking\bookinfo-gateway.yamlOnce the gateway is deployed successfully, you can get the external IP by using the below command:
kubectl get svc istio-ingressgateway -n istio-systemIt will return the following details about the gateway, including the external IP:
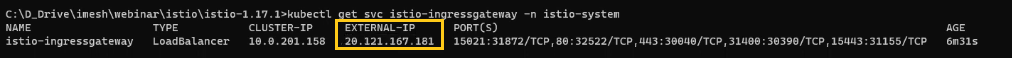
To access the application, we need to use http://<External IP>/productpage. "External IP" would be different in your case. Replace <External IP> with the IP returned in the previous step.
Here, accessing the link http://20.121.167.181/productpage from the web browser will open up a page like this:
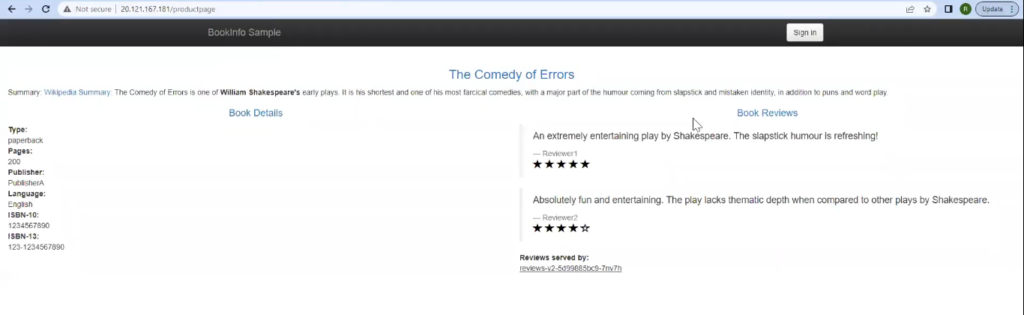
Note: If you look at the pods deployed in the cluster, you see that we have three versions (v1, v2, v3) for reviews. So, when you refresh the page, you will see changes in the reviews section.
Step #5: Visualize Service Graph Using the Kiali Dashboard
So, Istio has been deployed successfully, and the applications are working fine. Now, we can use the Kiali dashboard to visualize the traffic flow between pods and understand the dependency and topology graph. For that, we will need to deploy a few add-ons.
Run the following command to deploy the add-ons:
kubectl apply -f samples/addonsIt will deploy Kiali, Grafana, Prometheus, and a few other services.
Once they are deployed, use the below command to open the Kiali dashboard:
istioctl dashboard kialiThe above code will return a URL as you see below, which can access the dashboard:
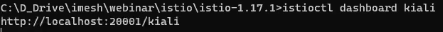
Accessing the URL from the web browser will open the dashboard with all the namespaces:
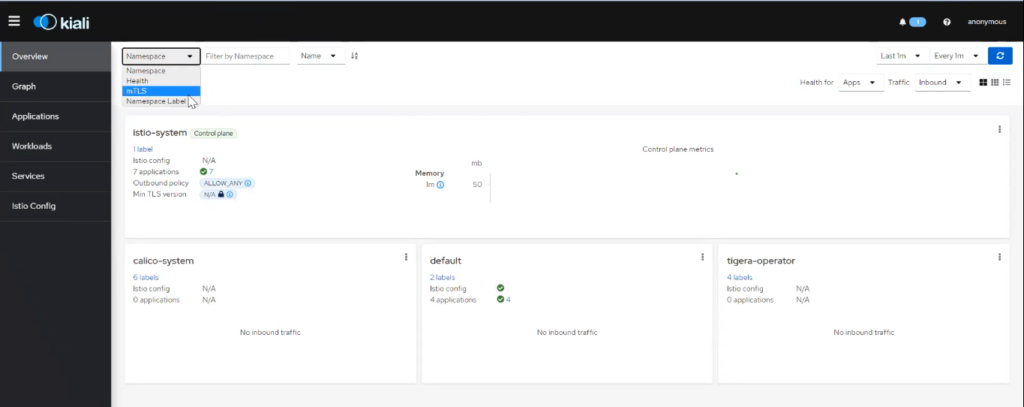
To see the service graph and visualize the traffic flow between services, you can go to “Graph” and then select the default namespace where we have deployed the applications.
It will open a service graph where you can see the request coming from ingress to the product page, which then flows to other microservices:
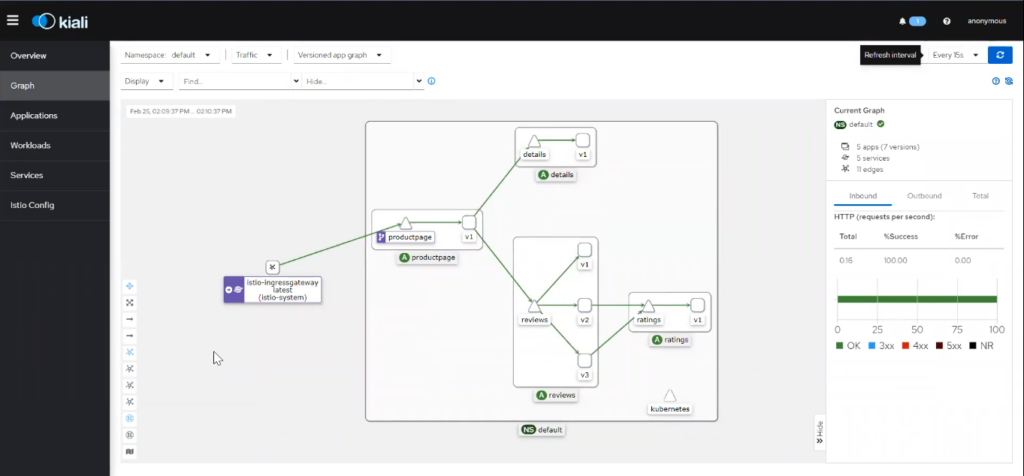
Conclusion
What we have seen here is a simple use case of Istio. We deployed Istio, a demo application, and visualized the traffic flow between services. In the real world, the network security logic required between microservices in a multicloud environment can be much more complex and granular. And Istio can certainly help to do that.

