Breach and Attack Simulation Technology (Short Version)
The ever-evolving cybersecurity landscape presents growing challenges in defending against sophisticated cyber threats. Managing security in today's complex, hybrid/multi-cloud architecture compounds these challenges. This article explores the importance of demonstrating cybersecurity effectiveness and the role of Breach and Attack Simulation (BAS) technology.
Challenges in Cybersecurity:
- Demonstrating cybersecurity ROI remains a challenge.
- Modern IT infrastructures are complex and prone to misconfigurations.
- Traditional vulnerability testing approaches (Penetration Testing, Red Teaming, Blue Teaming, Purple Teaming) are resource-intensive, manual, and offer only snapshots of security postures.
So, What's the Potential Answer?
Breach and Attack Simulation (BAS) Technology: BAS tools continually simulate attack scenarios, replicating real-world tactics, techniques, and procedures. They offer proactive vulnerability identification, security control evaluation, and incident response readiness improvement. BAS automates testing for various threat vectors and complements traditional testing methods.
The global BAS market is expected to reach $1.68 billion by 2027 - a 37.8% growth from 2018’s figures - primarily driven by demand for prioritizing security investments as vulnerability management grows ever more complicated.
BAS technologies were highlighted as one of the top solutions for CISOs to consider in a recent report from Gartner because of its effectiveness at testing against known threats.
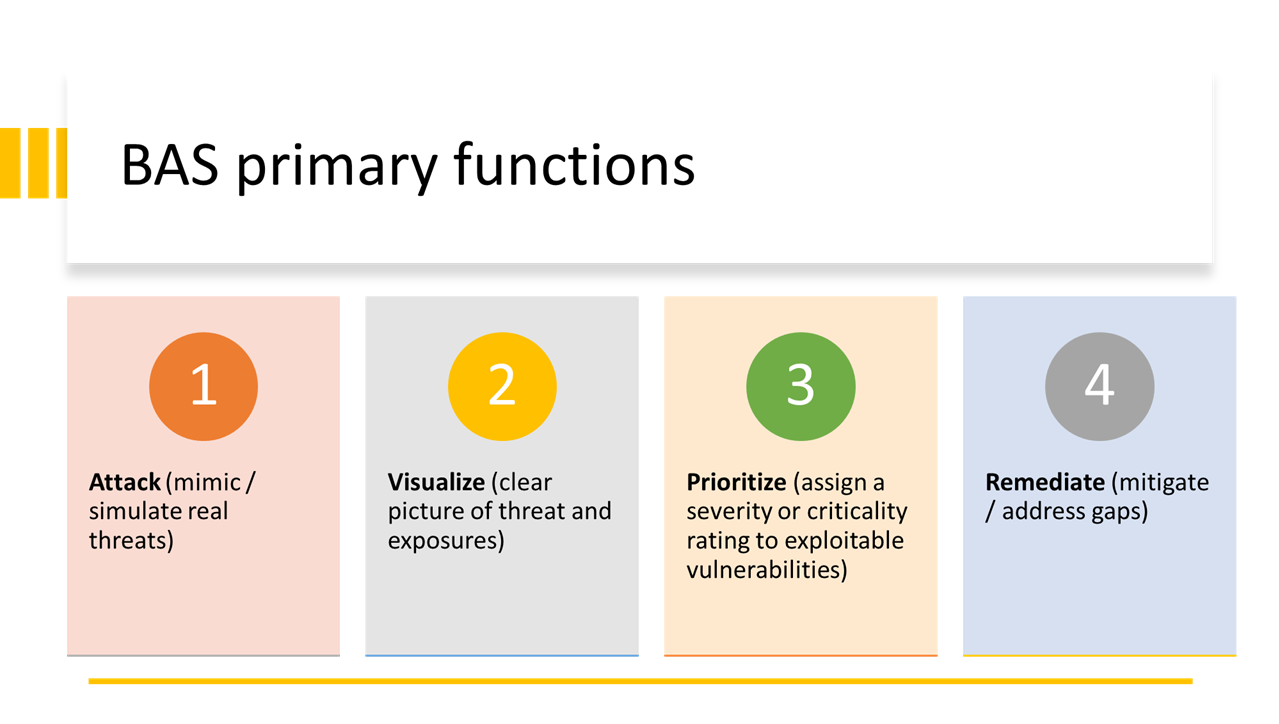
Where BAS differs from traditional approaches is in the use of closed-loop automation that allows IT/security teams to evaluate an environment for threat indicators and attack behaviors, unprotected assets, misconfigurations, human errors, log gaps, and basic IT hygiene issues. Armed with this information, security personnel can take the recommended actions to close gaps, fix misconfigurations, and strengthen credential management.

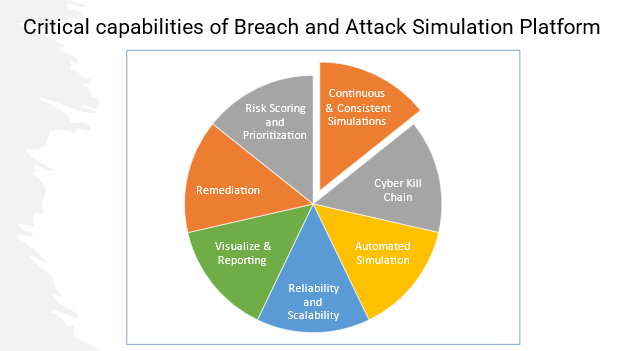
BAS Tool/Platform Needs Below Critical Capabilities
Real-World Use Case of BAS
To extract maximum value from the BAS tool/platform, the enterprise should plan to leverage the BAS tool for the below nine use cases:
- Attack Technique, Security posture, and readiness assessment
- Security control validation and efficacy
- Support for mergers and acquisitions
- Third-party assessments
- Complement penetration testing
- Risk-based vulnerability management
- Support for red and purple team activities
- Measurement of security operations processes
- Actionable Threat Intelligence
Find it interesting! Looking for technical details or a Solution Architect view, then read my full article "Securing Tomorrow: Unleashing the Power of Breach and Attack Simulation (BAS) Technology" here.
Summary
Breach and Attack Simulation (BAS) stands as a cornerstone of modern cybersecurity, providing enterprises with a powerful arsenal of features and functionalities. Not only does it serve as a litmus test for the effectiveness of security controls, but it also champions a proactive approach to cyber defense through automation. In today's security landscape, where the pursuit of cyber resilience hinges on vigilant monitoring and swift remediation, BAS emerges as a pivotal strategy to minimize the impact of threats on business operations.
Looking forward, BAS is poised to become an indispensable component of an enterprise's cyber defense strategy. However, for BAS to thrive in this dynamic landscape, it must embody above listed critical set of features and capabilities, both currently and in its future roadmap. Any deficiency in these elements could limit an organization's ability to harness the full potential of BAS technology. It is crucial to underscore that a BAS solution lacking these critical capabilities and integrations could mire an organization into confusion, resource drain, and potential disruptions to production services. Conversely, a fully featured and well-integrated BAS platform serves as a force multiplier, elevating security posture through profound insights into the attack surface and efficient remediation. Such an investment has the potential to pay for itself within a matter of months, empowering information security teams to enhance their effectiveness without the need for additional personnel or the purchase of additional security tools. In this ever-evolving realm of cybersecurity, BAS shines as a beacon of resilience, guiding enterprises toward proactive defense and heightened cyber preparedness.

