Microservices Security in a Nutshell
Microservices architectures have gained popularity due to their scalability, agility, and flexibility. However, with these architectures' increased distribution and complexity, ensuring robust security measures becomes paramount. The security of microservices extends beyond traditional approaches, requiring a comprehensive strategy to protect against evolving threats and vulnerabilities. Organizations can fortify their microservices architecture and safeguard sensitive data and resources by understanding the core principles and adopting effective security measures.
Introduction to Microservices
Microservices refers to a software development architecture style in which applications are created as a collection of small, independent services that connect via well-defined APIs (Application Programming Interfaces). Each microservice is responsible for a distinct business capability and may be created, implemented, and expanded independently of other services (Sascha Möllering, 2021). Microservices allow applications to be divided into smaller, manageable components, which can be independently scaled based on demand. This scalability enables organizations to respond quickly to changes and handle high-traffic loads more effectively.
By breaking down an application into smaller services, each with its bounded context and functionality, it becomes easier to understand, develop, test, and maintain the codebase. Developers can focus on individual services without impacting the entire application. Microservices promote fault isolation since a failure in one service does not necessarily impact the whole application. It enables graceful degradation and fault tolerance, as other services can continue functioning even if a particular service experiences issues.
Microservices allow organizations to choose different technologies, programming languages, and frameworks for various services based on their specific requirements. This flexibility encourages using the most appropriate tools and technologies for each service, improving overall development efficiency and effectiveness. Microservices facilitate decentralized development and deployment.
Multiple development teams can work on different services concurrently, and each service can be independently deployed, updated, or replaced without affecting other services or requiring a full application release.
With microservices, it is easier to implement continuous integration and continuous deployment (CI/CD) practices. Services can be developed, tested, and deployed independently, enabling faster release cycles and reducing the risk associated with large, monolithic deployments.
Microservices align well with cloud-native and distributed system architectures. They provide a natural fit for containerization and orchestration technologies like Docker and Kubernetes, making deploying and maintaining microservices on the cloud simpler.
Unlike traditional monolithic architectures, microservices offer greater flexibility, scalability, maintainability, and fault tolerance. These advantages have increased popularity in modern application development, particularly in organizations seeking to build robust, scalable, and agile systems.
A Brief History of Microservices
Microservices as an architectural style have evolved, influenced by various software development practices and technological advancements. The roots of microservices can be traced back to the concept of Service-Oriented Architecture (SOA), which emerged in the late 1990s and early 2000s. SOA aimed to create loosely coupled, reusable software services that could be orchestrated to build complex applications.
The advent of web APIs and the widespread adoption of cloud computing in the late 2000s and early 2010s played a significant role in shaping microservices. Web APIs allow easy integration and communication between distributed systems, while cloud platforms provide the infrastructure to host and scale applications.
The rise of DevOps practices and the focus on continuous delivery further influenced the evolution of microservices. DevOps emphasized collaboration between development and operations teams, promoting the need for smaller, independent components that could be developed, tested, and deployed more rapidly. The rise of DevOps practices and the focus on continuous delivery further influenced the evolution of microservices. DevOps emphasized collaboration between development and operations teams, promoting the need for smaller, independent components that could be developed, tested, and deployed more rapidly (Brown, 2018).
The Reactive Manifesto, published in 2013, emphasized the need for highly responsive, scalable, and resilient systems. This pushed developers to explore new architectural patterns, including microservices, to address scalability challenges associated with monolithic applications.
Netflix played a pivotal role in popularizing microservices through its success with a microservices-based architecture. In 2014, Netflix shared its experiences and best practices, highlighting the benefits of a loosely coupled, independently deployable service-oriented approach. In 2014, a software development thought leader, Martin Fowler published an influential article on microservices, which further brought attention to the architectural style. The report outlined microservices' key characteristics, benefits, and challenges, solidifying the concept within the software development community (Martin Fowler, 2014).
Over time, various frameworks, tools, and technologies have emerged to support microservices' development, deployment, and management. These include containerization technologies like Docker, orchestration platforms like Kubernetes, service discovery tools, API Gateways, and monitoring solutions. Microservices have gained significant traction recently, with numerous organizations adopting the architectural style. Companies like Amazon, Google, Uber, and Airbnb have embraced microservices to achieve scalability, flexibility, and agility in their software development and deployment processes.
It's important to note that microservices are not a one-size-fits-all solution and come with their complexities and challenges. However, their popularity has continued growing as developers and organizations seek to build modular, scalable, and resilient applications in an increasingly distributed cloud-native computing landscape (Brown, 2018).
Monolithic Application vs Microservices
Monolithic applications and microservices are two contrasting architectural styles used to build software applications. Most monolithic applications centrally enforce security, and individual components only need to worry about carrying out additional checks if necessary. Consequently, the security model for a monolith application is far easier than an application based on microservices architecture.
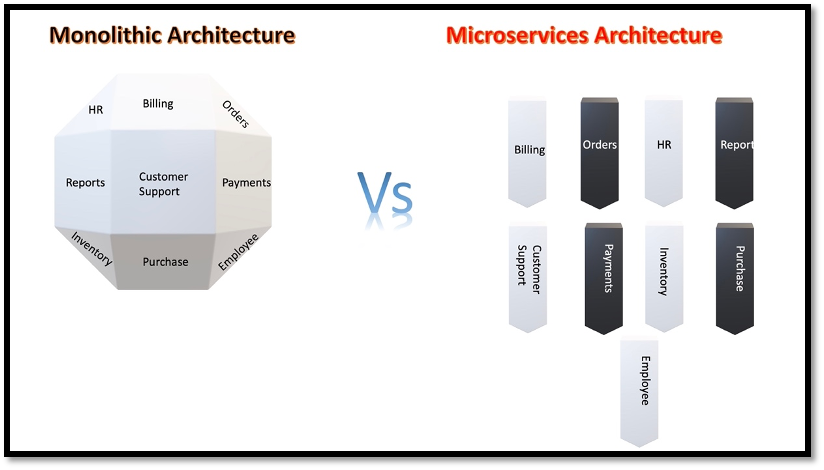
Fig.1.1: Monolithic vs microservices
Monolithic Applications
- Structure: Monolithic applications are built as a single, self-contained unit. All the components, such as the user interface, business logic, and data access layer, are tightly coupled and run within the same process.
- Deployment: The entire monolithic application is typically deployed as a single unit on servers or virtual machines. Scaling the application often involves scaling the monolith as a whole, which can be inefficient if specific components require more resources than others.
- Technology stack: Monolithic applications often use a single technology stack throughout, making it easier to develop and maintain. However, this limits flexibility in choosing different technologies for different components.
- Development and deployment: Development and deployment of monolithic applications usually follow a sequential process, where changes to one component may require redeploying the entire application; this can slow down development cycles and limit agility.
- Scalability: Scaling monolithic applications can be challenging as the entire application needs to be replicated, even if only a specific component requires additional resources; this can lead to inefficient resource utilization.
Microservices:
- Structure: Microservices break down an application into small, loosely coupled, independently deployable services. Each service focuses on a specific business capability and communicates with others through well-defined APIs.
- Deployment: Microservices can be deployed independently, allowing for scalability and flexibility. Each service can be scaled individually based on demand, improving resource utilization.
- Technology stack: Microservices allow different technology stacks to be used for various services based on their specific requirements. This provides flexibility and enables teams to choose the most appropriate technologies for each service.
- Development and deployment: Microservices promote independent development and deployment of each service. This enables teams to work on different services simultaneously and deploy changes without affecting other application parts.
- Scalability: Microservices offer better scalability as each service can scale independently based on its specific needs. This allows for efficient resource allocation and the ability to handle varying levels of demand for different services.
- Complexity: Microservices introduce complexity due to the distributed nature of the application and the need for inter-service communication. Managing network communication, data consistency, and overall system architecture can be challenging.
- Resilience: Microservices provide better fault isolation, as failures in one service do not necessarily impact others. This allows for more resilient systems that can handle failures without complete application downtime.
Choosing between a monolithic application and a microservices architecture depends on various factors, including the size and complexity of the application, scalability requirements, development team capabilities, and the project's specific needs. Monolithic applications offer simplicity and ease of development, while microservices provide scalability, flexibility, and agility (Martin Fowler, 2014). It's important to carefully evaluate these factors to determine the most suitable approach for a given project.
Securing Microservices
Addressing security concerns in microservices architectures is paramount. Microservices architectures often involve data exchange between multiple services. It is critical to ensure the security, integrity, and accessibility of sensitive data. Failure to address security risks could lead to unauthorized access, data breaches, or leakage of sensitive information.
Microservices architectures distribute application functionality across multiple services, which increases the attack surface. Each service becomes a potential entry point for attackers. Securing each service individually and implementing proper network security measures is essential to prevent unauthorized access and mitigate the risk of attacks.
Microservices rely heavily on APIs for communication between services, securing APIs is crucial to prevent unauthorized access, data tampering, or injection attacks (Goikhman, 2023). Organizations must implement proper authentication, authorization, and input validation mechanisms to ensure that only authorized services and users can access and interact with the APIs. Different teams typically develop and maintain microservices using various technologies and frameworks, this diversity can introduce potential vulnerabilities. Regular vulnerability assessments, code reviews, and penetration testing are essential to identify and address security weaknesses in each service. The organization should implement proper IAM practices to manage user identities and control access to microservices, and each service should have fine-grained access controls and enforce the principle of least privilege. Centralized authentication and authorization mechanisms, such as OAuth or JWT (JSON Web Tokens), can be utilized to ensure secure user authentication and authorization across services.
Microservices communicate with each other over networks, making secure communication vital, implementing secure protocols, such as HTTPS or TLS, ensures that data transmitted between services is encrypted and protected from eavesdropping or tampering (Goikhman, 2023).
Effective monitoring and logging mechanisms are crucial for detecting and responding to security incidents, centralized logging and monitoring solutions allow for real-time service activity monitoring, detecting abnormal behavior, and identifying potential security breaches. With the distributed nature of microservices, it is essential to implement threat detection and response mechanisms, intrusion detection systems (IDS), security event monitoring, and automated incident response systems can aid in the prompt identification and response to security incidents (Wajjakkara Kankanamge Anthony, 2020). Each microservice should undergo regular security testing, including penetration testing and vulnerability scanning, to uncover flaws and confirm the effectiveness of security safeguards. Security testing should be an integral part of the development and deployment lifecycle.
By addressing security concerns in microservices architectures, organizations can protect sensitive data, mitigate security risks, and maintain the trust of users and customers. It ensures the overall resilience, integrity, and reliability of the system, helping to prevent unauthorized access, data breaches, and other security incidents.
API Gateways in Securing Microservices
API Gateways play a crucial role in securing microservices architectures. They act as a centralized entry point for external client requests and provide various security features and capabilities. Below are key points of API Gateways' contributions to securing microservices:
- Authentication and Authorization: API Gateways handle authentication and authorization for incoming requests, they can enforce authentication mechanisms such as API keys, tokens, or OAuth, verifying the client's identity before allowing access to the underlying microservices. Centralizing these security controls at the Gateway simplifies the authentication process and reduces the burden on individual microservices (jamesmontemagno, 2022).
- Access control and permissions: API Gateways enable fine-grained access control and permissions management, they can enforce access policies, role-based access controls (RBAC), or other authorization mechanisms to ensure that clients only have access to the appropriate microservices, and operations based on their roles and privileges.
- Rate limiting and throttling: API Gateways help protect microservices from abuse and prevent denial-of-service (DoS) attacks by implementing rate limiting and throttling. They can enforce limits on the number of requests per second or minute from a specific client or IP address, ensuring fair usage and preserving the availability and performance of the microservices.
- Request validation and filtering: API Gateways can perform input validation and filtering to protect microservices from malicious or malformed requests, they can inspect and sanitize incoming requests, validating parameters, headers, or payloads to prevent common security vulnerabilities such as injection attacks or cross-site scripting (XSS).
- Encryption and transport security: API Gateways can handle encryption and transport security for incoming and outgoing requests, and they can terminate SSL/TLS connections, ensuring secure communication between clients and the Gateway. This helps protect sensitive data in transit and prevents eavesdropping or tampering.
- Logging and monitoring: API Gateways often provide logging and monitoring capabilities, capturing information about incoming requests, responses, and potential security events. Centralizing logs and monitoring data simplifies the detection and analysis of security incidents, aiding in forensic analysis, compliance, and proactive threat detection.
- Content filtering and transformation: API Gateways can apply content filtering and transformation to sanitize responses and protect against vulnerabilities, they can strip sensitive or unnecessary information from responses, modify payloads, or transform data formats to ensure that clients receive only the required data while protecting against information disclosure.
- Load balancing and high availability: API Gateways can handle load balancing across multiple microservices instances, distributing incoming requests to ensure optimal resource utilization and high availability. Balancing the load helps prevent individual microservices from being overwhelmed and provides redundancy for improved fault tolerance.
- API versioning and lifecycle management: API Gateways can assist in managing the lifecycle of microservices and versioning of APIs, and they provide a layer of abstraction that allows for evolving microservices without impacting clients directly. This helps manage backward compatibility, rolling out updates, and deprecating older versions in a controlled manner.
By incorporating these security features, API Gateways act as a perimeter around microservices, enforcing security policies and reducing the complexity of security implementation across individual services (jamesmontemagno, 2022). They enhance the overall security posture, visibility, and control over the microservices architecture.
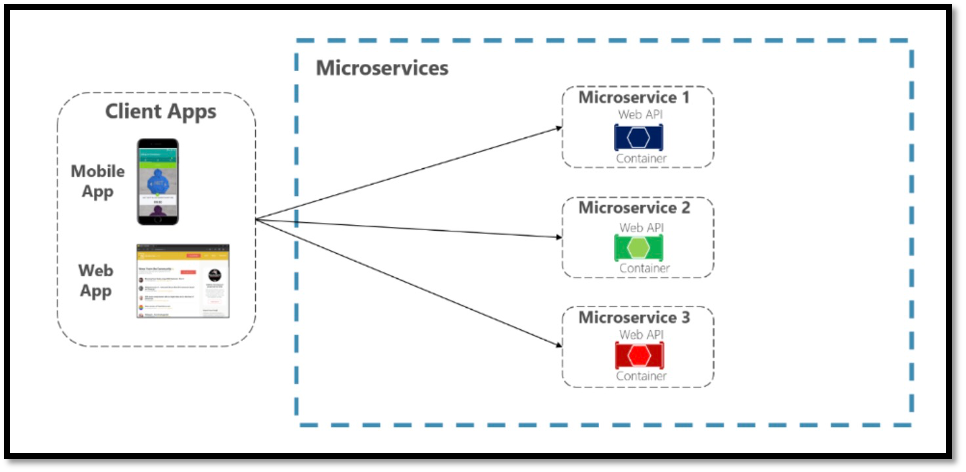
Fig.1.2: Direct client-to-microservice communication architecture without API Gateways (Source)
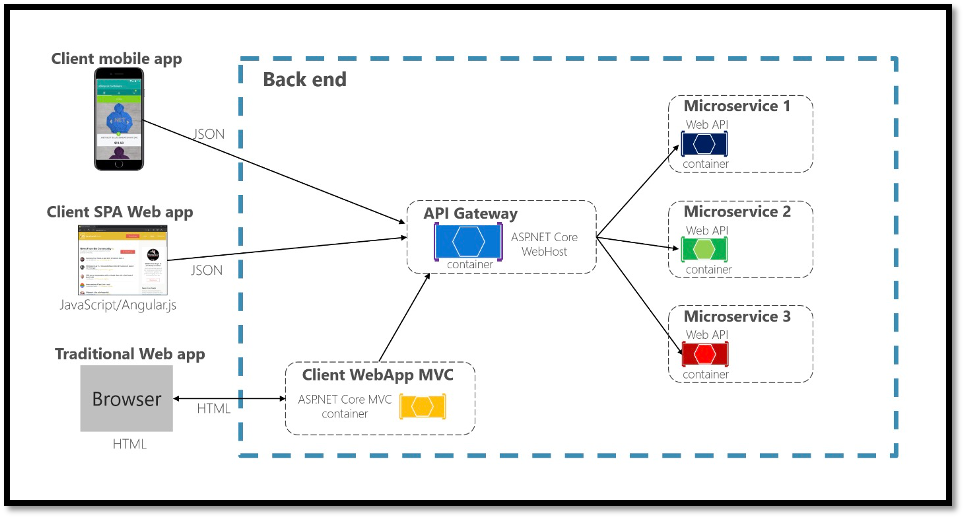
Fig.1.3: Using an API Gateway microservices communication (Source)
Challenges in Securing Microservice Architecture
Securing a microservice architecture comes with its own set of challenges due to its distributed and decentralized nature. Below are some common challenges organizations face.
- Authentication and Authorization: Managing authentication and authorization across multiple microservices can be complex. Ensuring that only authorized services and users can access specific microservices and their resources requires careful design and implementation of authentication and authorization mechanisms, this can involve technologies like OAuth, JWT (JSON Web Tokens), or API Gateways to enforce access control policies (Goikhman, 2023).
- Communication security: Microservices often communicate with each other over networks, making secure communication crucial. Implementing encryption and secure protocols (such as HTTPS) to protect data in transit between microservices helps prevent unauthorized access or tampering with sensitive information.
- Service discovery and identity management: As the number of microservices increases, maintaining an up-to-date registry of available services and managing their identities becomes challenging. Service discovery mechanisms and identity management solutions, such as service registries or service meshes, can help address these challenges and ensure secure communication between microservices.
- Distributed logging and monitoring: Monitoring the security of individual microservices and the overall system is vital, however, with numerous microservices, collecting and aggregating logs, metrics, and security events from various sources can be challenging. Establishing centralized logging and monitoring infrastructure to track and analyze security-related data helps detect and respond to security incidents effectively (Wajjakkara Kankanamge Anthony, 2020).
- Data security: Microservices often handle sensitive data, and ensuring its confidentiality, integrity, and availability is critical, implementing appropriate data protection measures such as encryption, access controls, and secure storage mechanisms becomes crucial. Additionally, defining data ownership and access policies to prevent unauthorized data access or leakage is essential.
- Code and dependency management: Microservices rely on numerous dependencies, including external libraries, frameworks, and third-party services, ensuring that these dependencies are secure and up to date with the latest security patches can be a challenge. Implementing robust code review processes, dependency management practices, and vulnerability scanning tools can help identify and mitigate potential security risks.
- Error handling and resilience: Microservices should handle errors and exceptions securely to avoid exposing sensitive information or providing attackers with insights into the system's vulnerabilities. Implementing appropriate error handling mechanisms, such as centralized error logging and secure error messages, helps maintain the system's resilience without compromising security.
- Secure deployment and DevOps practices: Microservices are typically deployed and updated independently, necessitating secure deployment practices. Ensuring secure containerization, infrastructure provisioning, and continuous integration/continuous deployment (CI/CD) pipelines are crucial to prevent security vulnerabilities during the deployment process.
- Threats to service interfaces: Microservices often expose APIs, making them potential targets for various attacks, such as injection, cross-site scripting (XSS), or denial-of-service (DoS) attacks. Applying robust API security practices, such as input validation, output encoding, rate limiting, and API versioning, helps protect the microservices' interfaces from security threats.
- Continuous security testing: Regular security testing is essential in a microservice architecture, traditional security testing techniques like penetration testing and vulnerability scanning may need to be adapted to address the distributed nature of microservices. Additionally, incorporating automated security testing into CI/CD pipelines ensures that security vulnerabilities are identified and addressed early in the development cycle (Wajjakkara Kankanamge Anthony, 2020).
Addressing these challenges requires a holistic and proactive approach to microservice security. It's important to consider security from the early stages of development and continuously monitor, assess, and improve the security posture of your microservices throughout their lifecycle.
Best Security Practices in Securing Microservice Architecture
Securing a microservice architecture involves implementing comprehensive security practices to protect the individual microservices and the overall system. Some best security practices to consider when securing a microservice architecture:
- Implement the principle of least privilege: Apply the principle of least privilege to ensure that each microservice has only the necessary permissions and access rights required to perform its specific functions. This reduces the risk of unauthorized access and limits the potential impact of a compromised microservice (8 Ways to Secure Your Microservices Architecture, n.d.).
- Use secure communication protocols: Employ secure communication protocols such as HTTPS/TLS to encrypt data transmitted between microservices. This prevents eavesdropping, tampering, and unauthorized access to sensitive information.
- Implement Authentication and Authorization: Use robust authentication mechanisms, such as OAuth or JWT, to verify the identity of microservices and users accessing the microservices. Implement fine-grained authorization controls to ensure only authorized entities can access specific microservices or perform particular actions.
- Apply input validation and output encoding: Validate and sanitize all input microservices receive to prevent injection attacks (such as SQL injection or cross-site scripting), similarly, encode output data to avoid potential security vulnerabilities and protect against attacks targeting consumers of the microservices' interfaces.
- Implement centralized logging and monitoring: Establish a centralized logging and monitoring system to collect and analyze logs, metrics, and security events from all microservices. This enables proactive threat detection, incident response, and forensic analysis during a security breach.
- Implement rate limiting and throttling: Protect microservices from abuse, excessive traffic, and denial-of-service (DoS) attacks by implementing rate limiting and throttling mechanisms. This helps ensure the availability and performance of the microservices while preventing resource exhaustion (Wajjakkara Kankanamge Anthony, 2020).
- Secure data storage and encryption: Apply appropriate encryption mechanisms to protect sensitive data at rest, whether stored in databases, caches, or file systems. Use robust encryption algorithms and securely manage encryption keys to safeguard data confidentiality.
- Conduct regular security assessments and penetration testing: Perform regular security assessments, vulnerability scanning, and penetration testing to identify and address security weaknesses in the microservices and their dependencies. This helps uncover potential vulnerabilities and allows for timely remediation.
- Secure configuration management: Ensure secure configuration management practices for the microservices and their underlying infrastructure components, use secure defaults, regularly update software versions, and follow security hardening guidelines to minimize the attack surface and reduce the risk of misconfigurations.
- Continuous security training and awareness: Promote a security-aware culture among development teams working on microservices, conduct regular security training sessions, educate developers about secure coding practices, and raise awareness about common security vulnerabilities and mitigation strategies.
- Implement fault-tolerant and resilient designs: Design microservices to be fault-tolerant and resilient to withstand attacks or failures, implement redundancy, failover mechanisms, and distributed load balancing to ensure the availability and continuity of the microservices.
- Secure third-party integrations: Vet and assess the security posture of third-party services or APIs that the microservices interact with, implement secure integration practices, validate and verify inputs from external sources, and ensure the integrations follow secure communication standards.
Security in a microservice architecture is an ongoing effort. It requires a combination of secure coding practices, secure infrastructure configuration, regular testing, and continuous monitoring to ensure the system's overall security.
Conclusion
Microservices architectures offer immense benefits in terms of scalability and agility, but they also introduce unique security challenges. By implementing a comprehensive security strategy encompassing authentication, authorization, secure communication, and monitoring, organizations can ensure the integrity, confidentiality, and availability of their microservices infrastructure. Embracing a security-first mindset will enable businesses to build resilient and trustworthy microservices architectures in today's dynamic and evolving threat landscape.
References
- 8 Ways to Secure Your Microservices Architecture
- Beyond buzzwords: A brief history of microservices patterns: Brown, K. (2018, October 10)
- How to secure microservices: the complete guide: Goikhman, E. (2023, Feb 2)
- The API gateway pattern versus the Direct client-to-microservice communication: jamesmontemagno, a. g. (2022, September 20)
- Microservices: Martin Fowler, J. L. (2014, March 25)
- Implementing Microservices on AWS: Sascha Möllering. (2021, November 9)
- Microservices Security in Action: Wajjakkara Kankanamge Anthony, N. D. (2020), Manning Publications

