Cloud Computing Security: Ensuring Data Protection in the Digital Age
Data security is significant in today's digital landscape, especially when it comes to cloud computing. This cannot be emphasized enough. With people and organizations moving their operations and data to the cloud, it is important to have strong security against cyber attacks.
In modern-day operations cloud services have become crucial, offering scalability, flexibility, and cost-effectiveness. However, this increasing dependence on cloud services also brings about a plethora of security issues.
Challenges encountered in ensuring data protection in cloud computing environments will be examined in this article, while also exploring procedures to overcome these challenges and strengthen security measures.
Cloud Computing Security
Cloud computing has completely changed the way organizations function by offering a convenient and flexible solution for data processing, storage, and access. Protecting sensitive data is convenient, but it also necessitates strong security procedures.
The delivery of computing services over the Internet, such as databases, storage, software, networking, and analytics, is referred to as cloud computing. Three essential components—Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS)—each offer a variety of degrees of administration and control.
A variety of security security risks and threats, including malware, illegal access, insider threats, and compliance violations, can affect cloud environments. These risks may be made worse by the shared nature of cloud infrastructure and the dependence on third-party providers.
To maintain things discreetly Information availability, integrity, and cloud computing all depend on data protection. Strong security measures including encryption, access limits, audits regularly, and monitoring may help lower risks and enable regulatory compliance.
Understanding cloud computing security is essential for organizations to make use of the cloud's advantages while protecting against possible threats and vulnerabilities. Businesses may win the trust of their stakeholders and customers by putting data protection measures first and operating safely in the digital landscape.
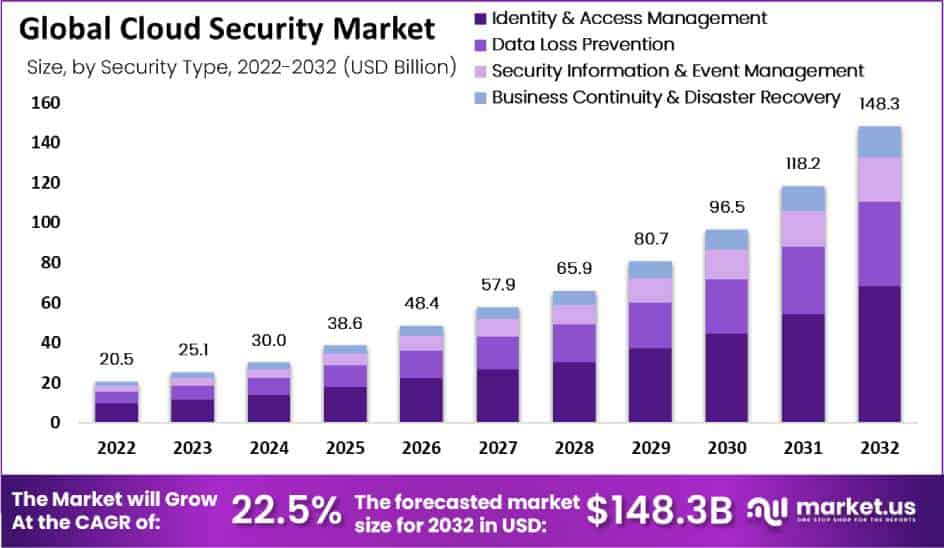
The Global Cloud Security Market size is expected to reach USD 148.3 billion by 2032, exhibiting an impressive CAGR of 22.5% between 2022 and 2032, from its current value of USD 20.5 billion in 2022.
Common Security Challenges in Cloud Computing
As cloud computing continues to transform the digital world, it brings up a lot of security problems that organizations must deal with to protect their data and operations.
- Data breaches and unauthorized access: Data breaches and unauthorized access risk are one of the foremost concerns in cloud computing. Vulnerabilities can be exploited by hackers to gain access to sensitive information, posing a significant threat to data integrity and confidentiality.
- Insider threats and data loss: Unintentional revelation of data by contractors or workers with access to delicate information might prompt information misfortune or spillage because of malicious activity. Whether purposeful or inadvertent, Insider dangers are a crucial risk to cloud security.
- Vulnerabilities in shared infrastructure: As an assault on one user's information or application might influence others having a similar infrastructure, this shared model presents weaknesses. Cloud conditions ordinarily depend on a shared framework, permitting a few users to share assets and services.
Organizations can ensure a safe modernized climate and control the perils related to cloud computing. Keeping an eye on these standard security issues is critical for firms to oversee dangers and safeguard their resources in the cloud, Through the execution of solid safety efforts, remaining steady with rules, and enabling a culture of safety care.
Strategies for Enhancing Cloud Computing Security
Offering unmatched adaptability and versatility, cloud computing has become essential for present-day organizations. With this comfort comes the obligation of guaranteeing strong security measures to protect delicate data and operations. Here are a few techniques to upgrade cloud computing security.
- Encryption and data masking techniques: Encryption and information covering techniques ensure that confidential data is protected while it is in transit and at rest. Businesses may reduce the risk of unauthorized access and information breaches by encrypting data before it is stored in the cloud and using masking to hide sensitive information.
- Identity and access management (IAM) solutions: IAM solutions play a critical part in controlling admittance to cloud resources. By executing solid authentication mechanisms, for instance, multi-factor authentication (MFA) and role-based access control (RBAC), organizations can uphold granular access policies and lessen the risk of unapproved access.
- Continuous monitoring and threat detection: Regular inspections and attack detection features enable enterprises to identify and react to security breaches instantly. Organizations may prevent security incidents by employing assault intelligence feeds and security information and events management (SIEM) technologies to identify suspicious exercises in advance.
- Secure configuration and patch management: Guaranteeing secure configuration and timely patch management is fundamental for safeguarding cloud infrastructure against vulnerabilities. By consistently evaluating cloud configurations, applying security best practices, and instantly fixing known vulnerabilities, organizations can diminish the risk of exploitation by malicious actors.
- Disaster recovery and backup planning: Despite the best security measures, incidents such as data breaks or disastrous occasions can regardless occur. In this way, having areas of strength for a recovery and backup plan set up is fundamental. By reliably backing up data, testing debacle recuperation methodology, and staying aware of obvious dullness across various geographic areas, organizations can restrict downtime and information loss if there should be an occurrence of a security incident.
Embracing these procedures can generally redesign cloud computing security and engage organizations to use the greatest limit of the cloud while lightening risks effectively. By zeroing in on safety efforts and staying vigilant against arising attacks, organizations can foster trust with their clients and accomplices and work securely in the computerized age.
Best Practices for Data Protection in the Cloud
Guaranteeing the security of sophisticated data is crucial in an era when organizations are driven by it. The increasing use of cloud computing means robust methods for protecting sensitive data must be implemented. A few recommended methods for cloud information security are as follows:
- Encryption: Encrypting data both at rest and in transit adds a layer of security, making it unreadable to unapproved users. Use solid encryption algorithms to shield delicate data from possible breaches.
- Data backup and recovery: Lay out a vigorous data backup and recuperation intended to guarantee business continuity in case of data loss or a security breach. Routinely backup your data to get offsite locations and test your backup technique to guarantee they are successful.
- Regular audits and monitoring: Conduct ordinary reviews of your cloud environment to recognize security holes and vulnerabilities. Carry out nonstop monitoring solutions to detect dubious activities and potential security assaults in real time.
- Access control: Execute unbending access controls to coordinate who can get to your information in the cloud. Use role-based access control (RBAC) to appoint assents considering clients' jobs and obligations, restricting the risk of unapproved access.
- Multi-Factor Authentication (MFA): Authorize multi-factor authentication for getting to cloud services, anticipating that clients should give different sorts of checks prior to acquiring entry. This adds a layer of security and hinders unapproved induction to your data.
- Employee training and awareness: Show your staff security best practices and stress the value of cloud data confirmation. Advance a security cognizant culture to ensure that specialists stay careful against any attacks.
Final Thoughts
We've covered the basic techniques and industry guidelines for safeguarding your data in the cloud here. Each kind of preparation is vital for decreasing risks and safeguarding delicate data, from solid authentication and access limitations to frequent security assessments and working with trustworthy vendors.
The need to give cloud security a top concern in business strategies is simply going to increase as development advances. To diminish risks, organizations need to make critical investments in security protocols, train workers on security awareness, and team up with solid cloud expert cooperatives.
A comprehensive strategy that combines participation, careful planning, and a promise of continuous progress, should be adopted to safeguard your data in the cloud. safeguarding your data, reducing risks, and ensuring the long-term viability of your organization by focusing on cloud security and adopting the accepted methodology by adopting the suggested practices and focusing on cloud security in your processes.

