How to Set up OAuth JWT Flow and mTLS in the Salesforce Connector for a MuleSoft App
In the first part of this series, we set up a Mule app and a Salesforce Connected app for the OAuth JWT bearer token flow. In this second part, we’ll go through the required steps to set up mutual TLS between the Mule app and the Salesforce Connected App we created in that first post.
Create a New Profile in Salesforce for mTLS
- If the Profile you used in Part 1 of this guide (linked earlier) is the definitive one that you’ll use for this Mule app, skip this step.
- Go to Setup > Profiles.
- Click on New Profile.
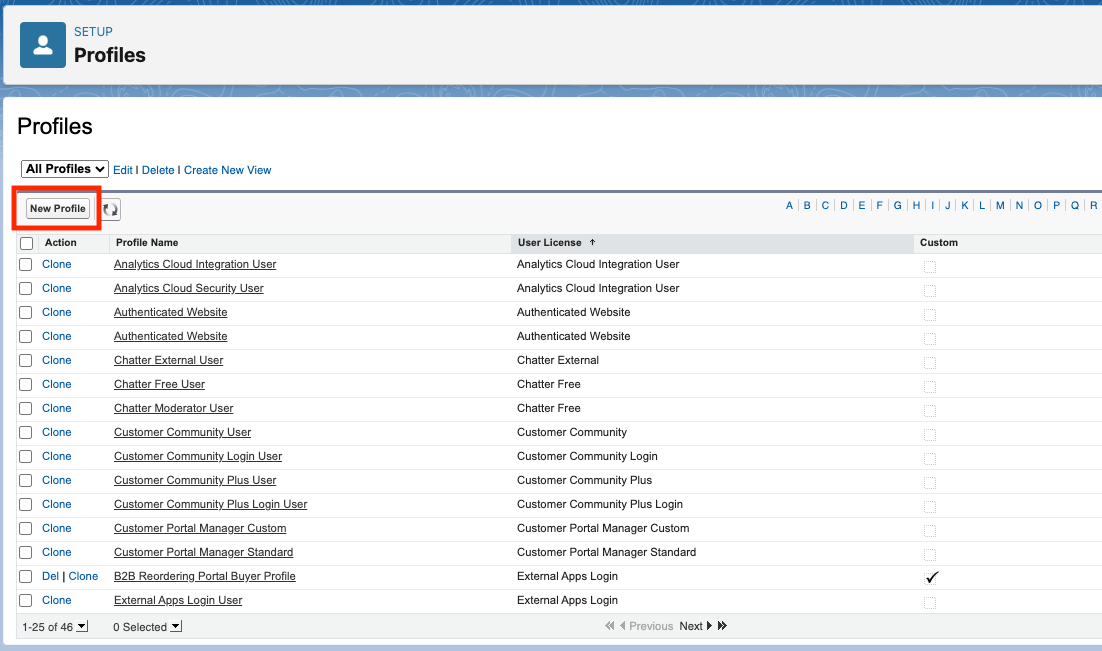
- Pick up an existing profile to clone from and give it a name. We’ll clone the System Administrator profile in this example, just for the purpose of the demonstration. As a best practice, pick up an Integration User Profile or an existing profile associated with the Named Users you’re planning to use from the Mule App.
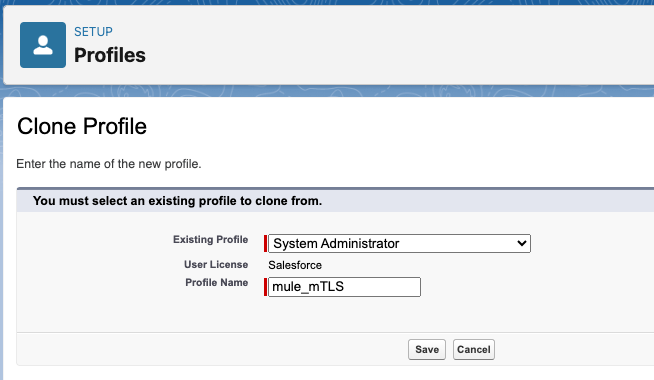
- Click Save.
- Go back to the Profile Overview page, scroll down to the System section, and click on System Permissions.
-
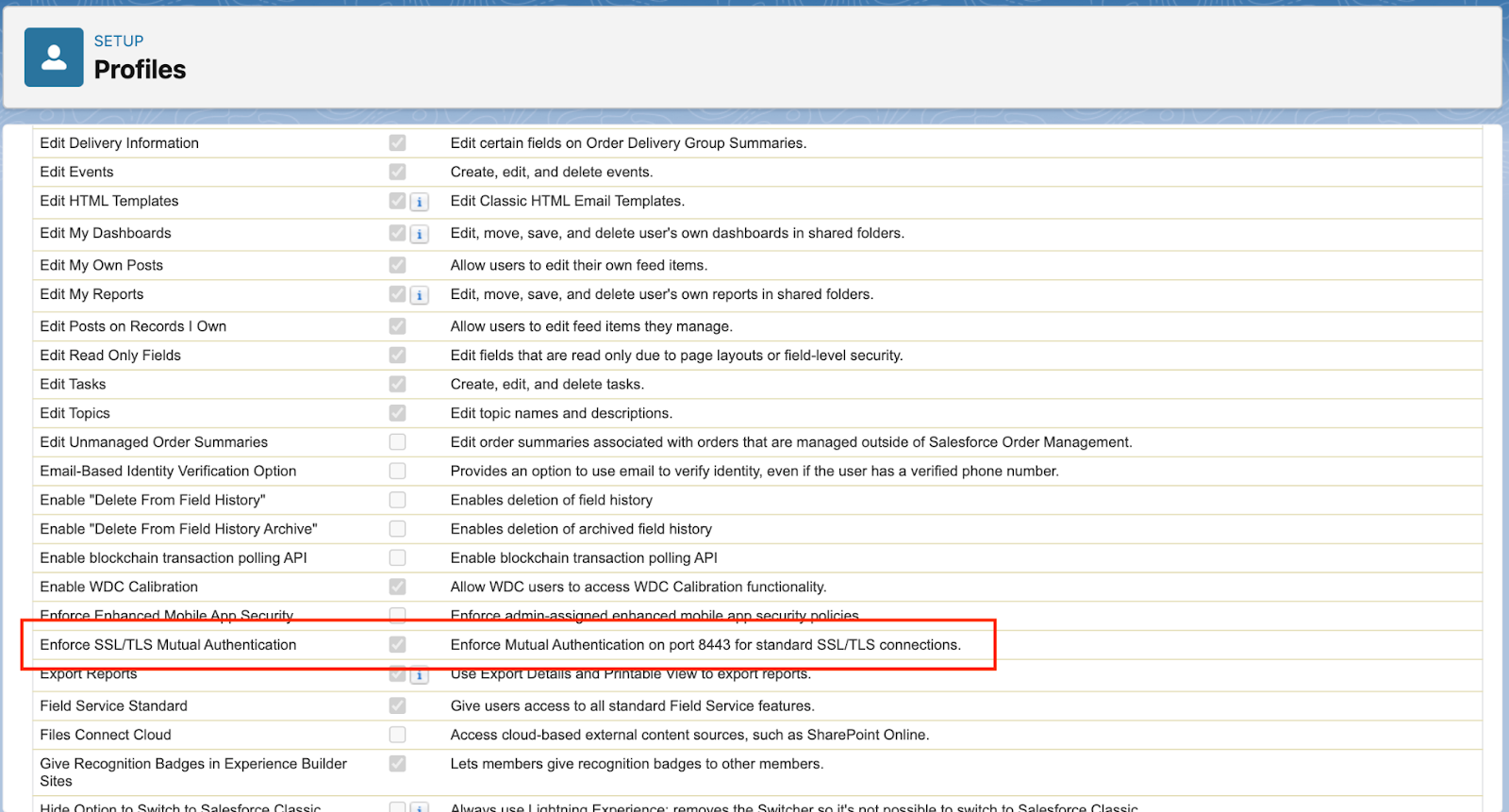
Add the Enforce SSL/TLS Mutual Authentication from the list of permissions. If you don’t see this option you need to contact Salesforce to enable the feature.
- Assign a user to the new profile. That would be the user (or users) that we’ll use in the Mule app. Depending on your use case it can be a Named User or an Integration User.
- Go to Setup > Users and click on your selected user.
- In the User page click on Edit and change the Profile to our newly created profile for mTLS.
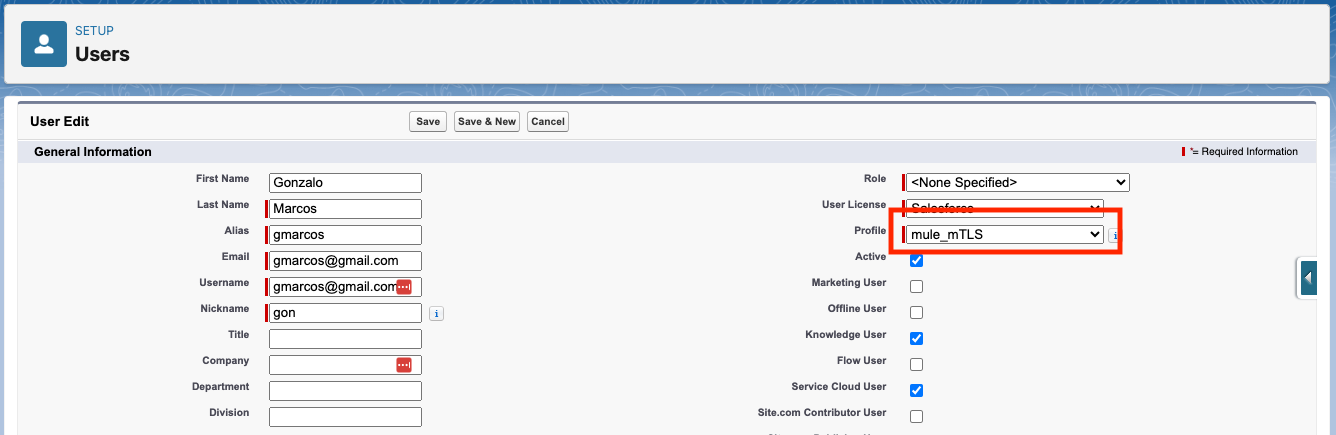
- Click Save.
(Optional) Create a Connected App Associated With This Profile
- Skip this step if you’ll be using the Connected App created in Part 1.
- If not, follow the steps in Part 1 to create a new Connected App and the configuration of the Mule app to use OAuth JWT as auth flow in the salesforce connector.
Set Up a Mutual Authentication Certificate
-
Go to Setup > Certificate and Key Management and click on the Upload Mutual Authentication Certificate within the Mutual Authentication Certificates section. If you don’t see this section in the Certificate and Key Management page you’ll need to open a support ticket with Salesforce to get this feature enabled in your org.
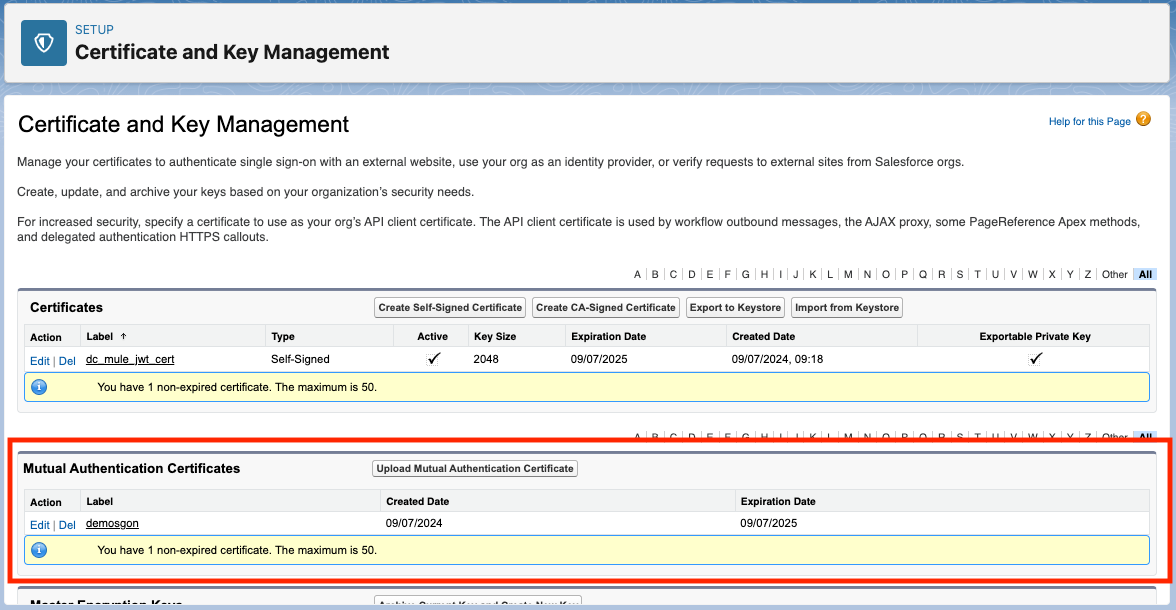
- Provide a name and a label for your certificate and then add the certificate. Remember that self-signed certificates are not valid for mTLS. Here, we’ll be uploading the certificate with the public key for your user(s) in the Mule App. The corresponding private key will be stored in the Mule app.
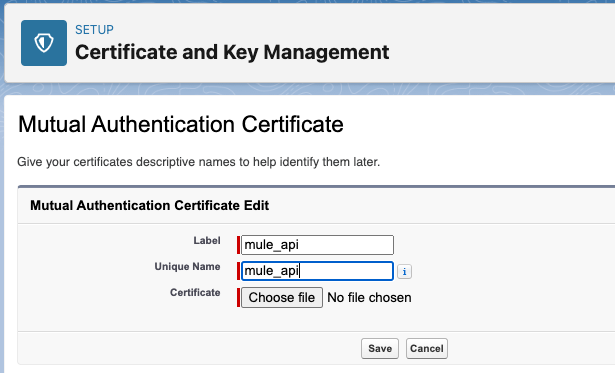
- You must upload a PEM-encoded client certificate. You only need to upload the client certificate itself; do not upload a certificate chain.
Configuration of the Mule App
In this section, we’ll continue with the mule app created in Part 1 of this guide. Refer to that part if you need to start with a new mule application.
Upload the Key Store to the Mule Project
- Go to your Mule app in Anypoint Studio.
- If you haven’t done it, create a key store that will include your private/public key pair. You can do it as a JKS, PKCS12 or JCEKS. All of them are valid. In this guide, we’ll use JKS. You can use any tool such as Key Store Tool.
- Right-click on the project name and select Show In > System Explorer. That should open an explorer window in the main folder of our project.
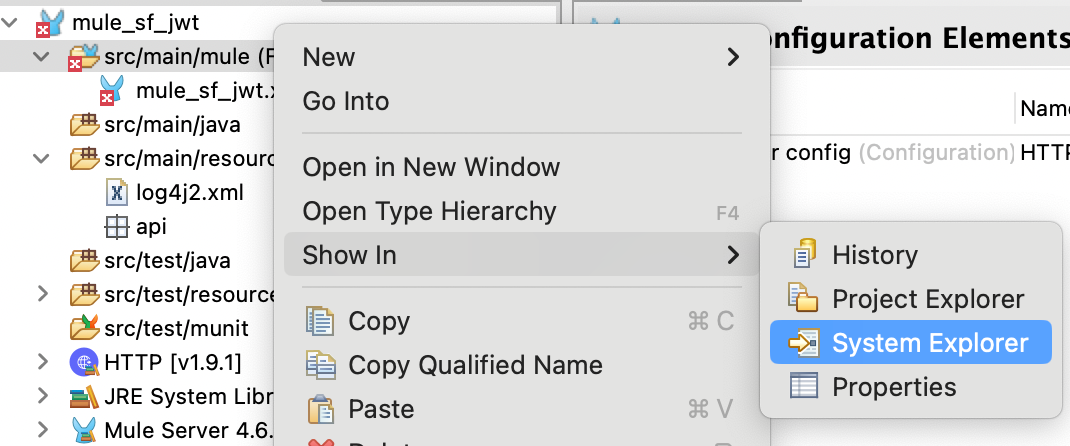
- From there, go to Resources and upload the jks file of our keystore.
- Back to Studio: If you right-click again in the name of our project and click Refresh, we should see our keystore under the src/main/resources folder.
Set up the Key Store in the Salesforce Configuration Element
- Next, from the canvas, go to the Global Elements tab and open the Salesforce Config element.
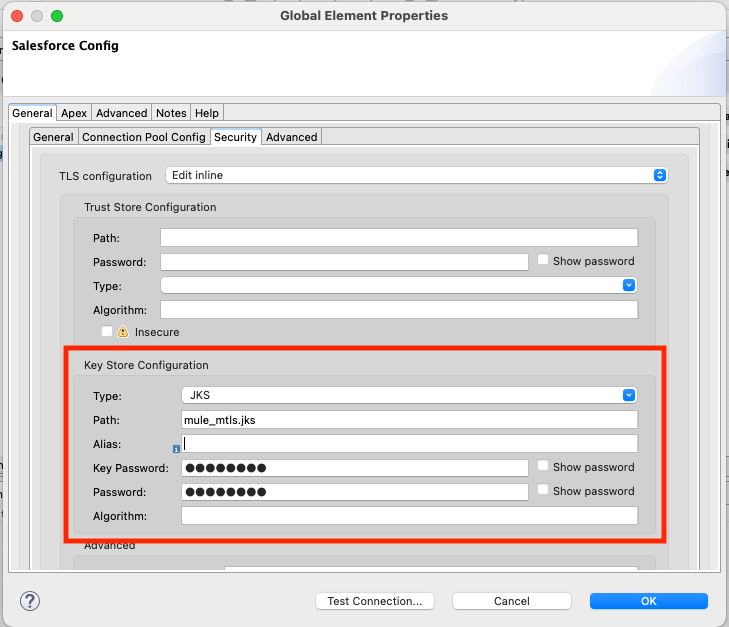
- Go to the Security Tab and select the Edit Inline option in the TLS configuration dropdown (or select global reference if you prefer to set this configuration as a Global Configuration Element).
- In this tab, we need to provide the Key Store for the User(s) that will be accessing our Salesforce Connected App via the Salesforce connector in our mule app. The key store has to contain the private key corresponding to the public key and certificate that we uploaded in our previous step in Salesforce as a Mutual Authentication Certificate.
- Select the type of Key Store; in this guide, it is JKS.
- The path within the app of the key store: The root path corresponds to the src/main/resources folder in our Mule Project. In our example, we uploaded the key store in that root folder
- Provide the password for your keystore.
-
Test the connection:
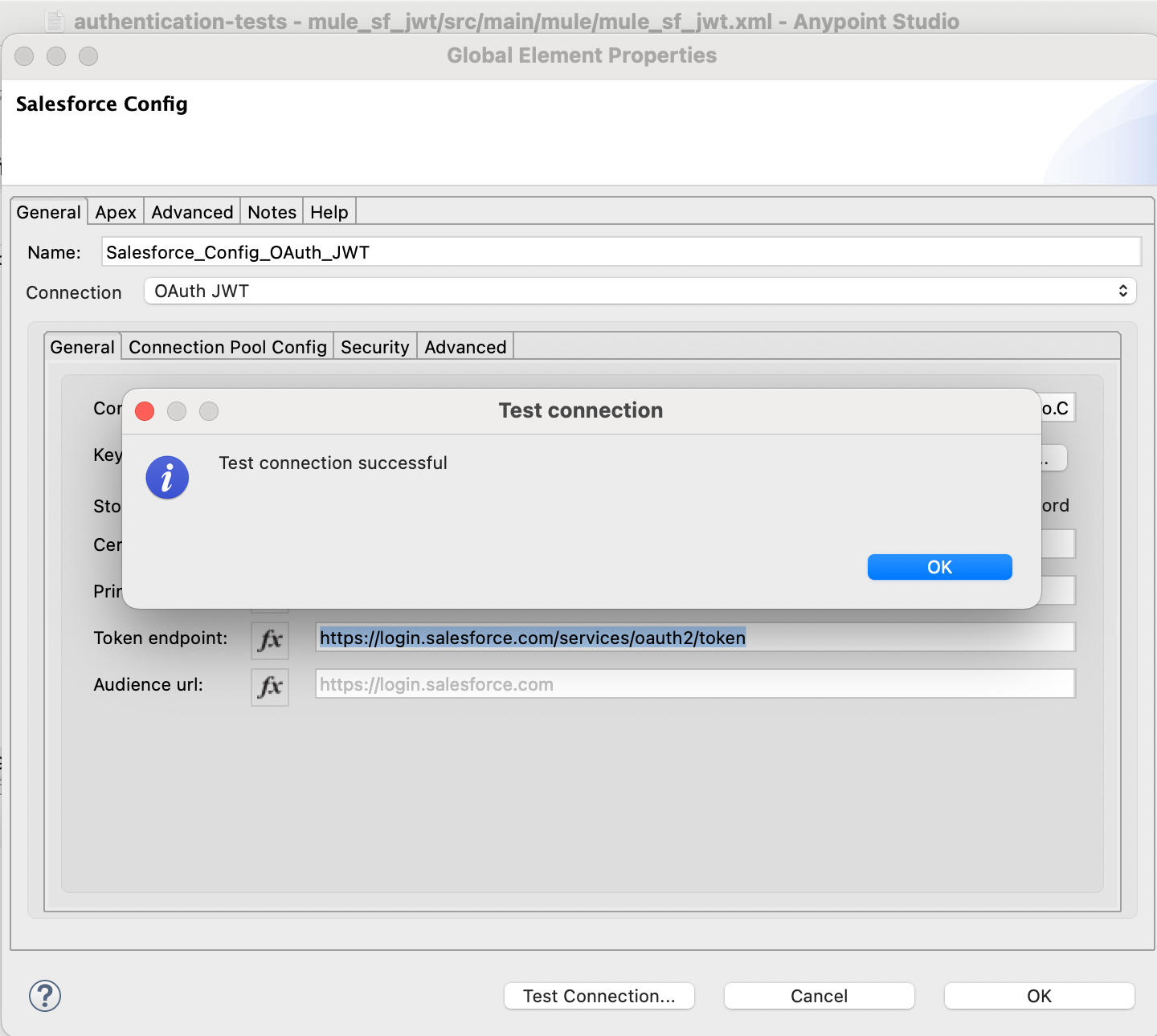
- Run the app in Studio.
- Test the app and verify that your Salesforce query is successful.
Video
You can also follow this video tutorial from our Mulesoft Ambassador, Stefano Bernardini:

