Multicluster Gateways With Kubernetes Gateway API
Kubernetes Gateway API is the new specification released by CNCF to standardize the Kubernetes Ingress traffic. Now, what if a service is configured as High Availability (HA)? (Say it is in a different cloud environment and you have to access it from the Gateway; i.e., multicluster, multi-cloud scenario.) In this article, we will showcase how to use the Gateway API spec to configure gateways for multicluster setup.
Multicluster Kubernetes Gateway Demo Overview
We have two clusters: one in EKS (primary) and the other in GKE (remote). I have deployed Istio in both the clusters and the setup is primary-remote Istio installation. Istio is used as the controller to implement the Gateway API resources.
Here’s what I’m going to do:
- In the primary cluster/EKS, deploy the
helloworld-v1deployment,helloworldservice, andechoserverservice. - In the remote cluster/GKE, deploy
helloworld-v2deployment,helloworldservice,echoserverdeployment, andechoserverservice. - Deploy the Kubernetes Gateway API resources —
GatewayandHTTPRoutes— in the primary cluster. - After the deployments, we will verify that the Gateway in the primary cluster/EKS can access the services in the remote cluster/GKE, as shown in the image below:
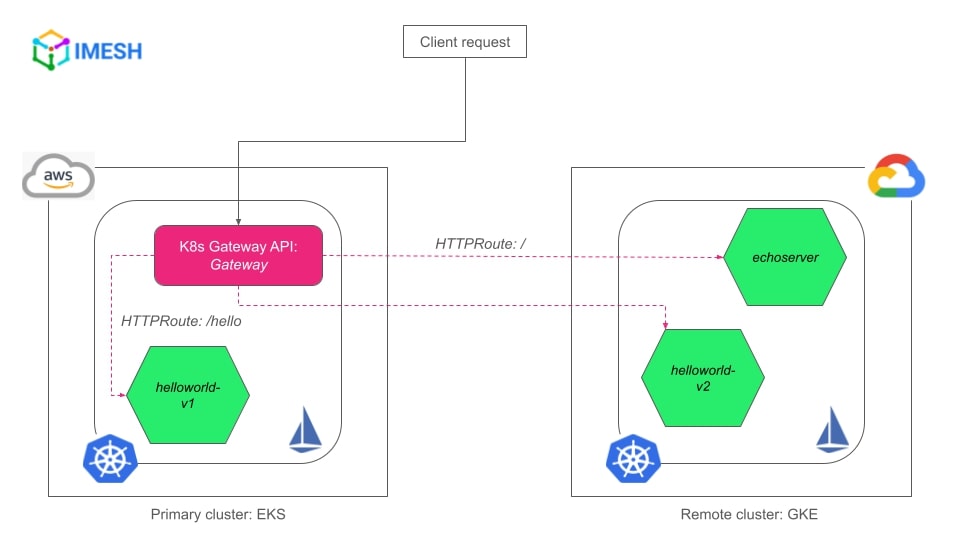
Multicluster, multi-cloud Gateway with K8s Gateway API demo setup
Deploy the Applications and Services in Clusters
Deploy helloworld-service in both the primary and remote clusters:
kubectl -f apply helloworld-service.yaml --context=eks-cluster
kubectl -f apply helloworld-service.yaml --context=gke-clusterkubectl -f apply helloworld-deployment-v1.yaml --context=eks-cluster
kubectl -f apply helloworld-deployment-v2.yaml --context=gke-clusterkubectl -f apply echoserver-service.yaml --context=eks-cluster
kubectl -f apply echoserver-service.yaml --context=gke-cluster
kubectl -f apply echoserver-deployment.yaml --context=gke-cluster
Note that service resources need to be deployed in both clusters for this to work. That is why I deployed the echoserver-service in the primary cluster/EKS although the deployment is only in the remote cluster/GKE.
Now, let us verify the deployments in both the primary and secondary clusters:
kubectl get svc -n demo --context=eks-cluster
kubectl get pods -n demo --context=eks-cluster
kubectl get svc -n demo --context=gke-cluster
kubectl get pods -n demo --context=gke-cluster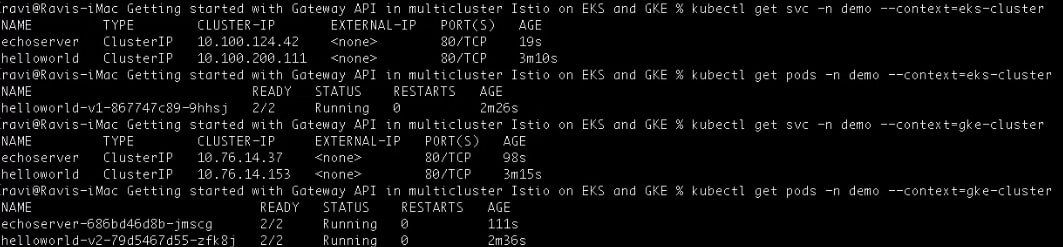
The primary cluster has the helloworld-v1 pod running, while the remote cluster has both helloworld-v2 and echoserver pods running successfully:
Deploy K8s Gateway API Resources and Verify Multicluster Communication
Apply the gateway resource in the primary/EKS cluster:
kubectl apply -f gateway-api-gateway.yaml --context=eks-clusterThe Gateway uses Istio as the controller and is deployed in the istio-ingress namespace.
Deploy HTTPRoute in the primary cluster for the helloworld application, which listens on path /hello:
kubectl apply -f helloworld-httproute.yaml --context=eks-clusterNow, let us verify multicluster communication by curling the helloworld application; but first, we need to get the Gateway IP:
kubectl get svc -n istio-ingress --context=eks-clustercurl your_gateway_external_ip/hello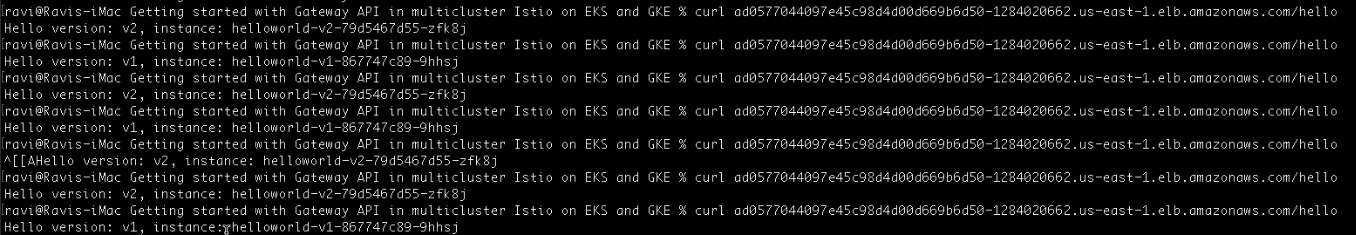
You can see that the request is served by both the helloworld-v1 and helloworld-v2 that are deployed in the primary and secondary clusters, respectively.
Now, let us deploy the HTTPRoute for echoserver in the primary cluster, which listens on / :
kubectl apply -f echoserver-httproute.yaml --context=eks-cluster
Verify if the Gateway is able to access echoserver deployed in the remote cluster:
curl your_gateway_external_ip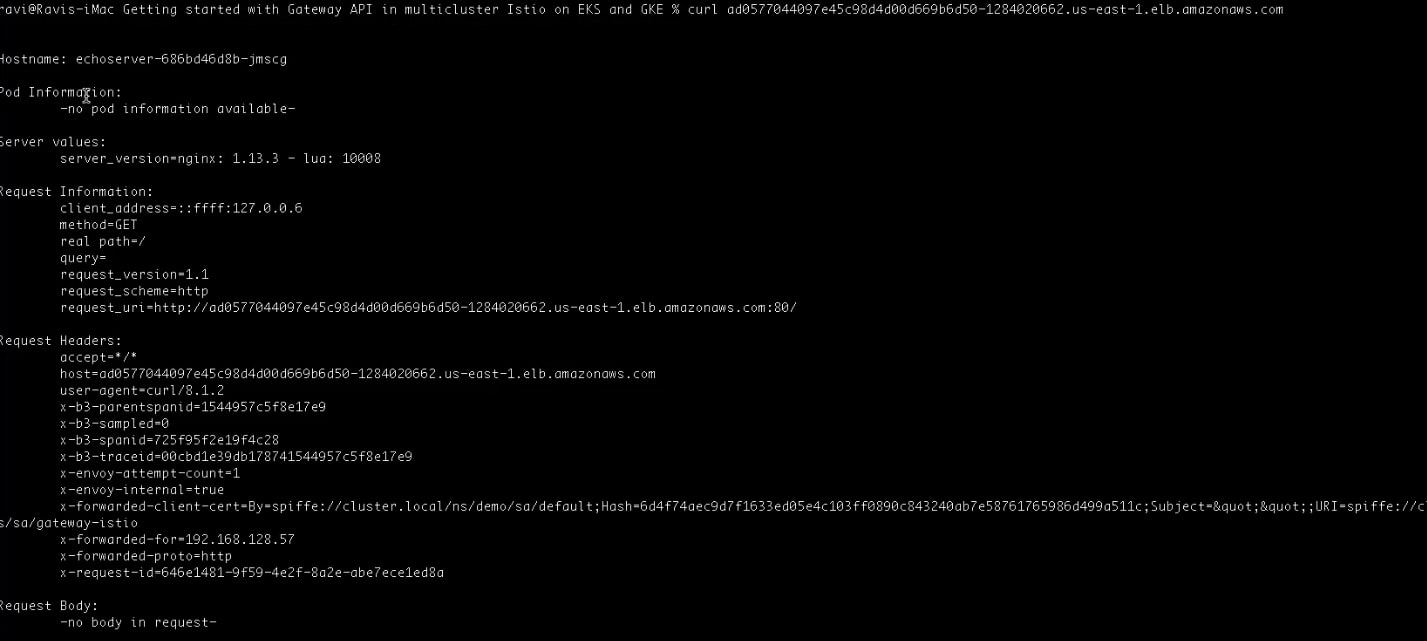
The Gateway is able to get a response from echoserver deployed in the remote cluster successfully. And that is the end of the demo.

