Demystifying Security on AWS Cloud

As of today, every organization is adopting a cloud-first approach for hosting their business applications. Those who had their applications in data centers are also migrating their assets to cloud. Some of the reasons are:
There are limited upfront capital costs compared to traditional days where you need space to host your infrastructure in data center and need a lot of money to own and manage it.
You pay for what you use.
Easy scaling - During peak hours or festive time, you can easily scale up and down your capacity based on the workload.
And there are many more due to which more and more organizations are moving their applications to Cloud platforms.
You may also enjoy: AWS Cloud Security Best Practices
According to Forbes, digitally transforming enterprises is a big reason behind large cloud adoption. While the adoption has increased, so have the challenges with “Security” being the biggest challenge for them to move to cloud.
Data breaches that are exponentially increasing every day. A small misconfiguration by accident could lead to a disaster.

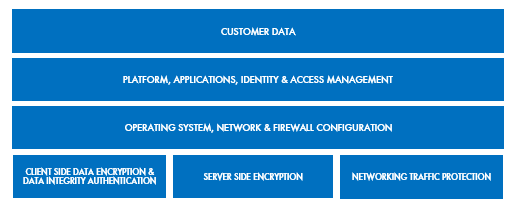
Now we know why security is important, let’s shift our focus to how we can protect our assets on a cloud platform like AWS. Over the years, AWS has been heavily investing on developing various security-based services that you can use to secure your application, platform, network, data from unauthorized access and malicious attacks. As part of the AWS Shared Responsibility model, the customer is responsible for security “IN” the cloud for the following:
On AWS, you can make use of the following security, identity and compliance services that can help you build a better and secure platform on AWS.
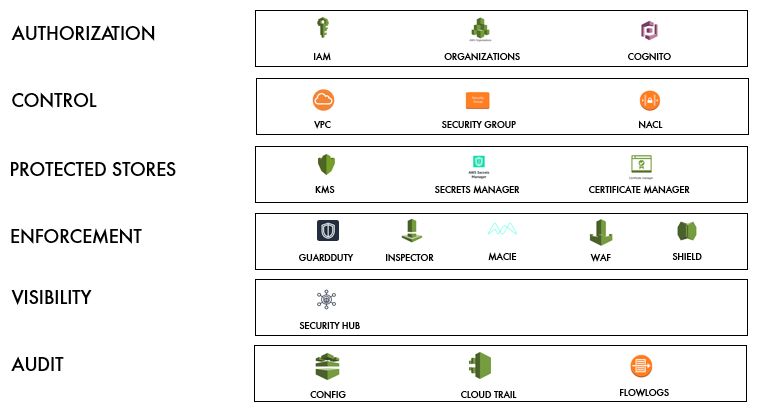
IAM |
Use Identity and Access management to restrict users, teams the access to AWS services at a granular level. You can also have password policy management and MFA enabled for every user. |
Organizations |
Organizations help you to central govern your environments when your workloads are increasing. You can centrally manage billing, access control, security and compliance across multiple AWS accounts you are managing. |
Cognito |
Cognito helps you in adding user sign-up, sign-in, and access control to your web and mobile apps quickly and easily. |
VPC |
With VPC, you can build your own secure network with routing policies, firewalls, rules, etc. |
Security Groups |
Security groups are firewalls for your VPC. They are helpful when you have to define access restrictions at port and instance level. |
NACL |
NACLs are used to define access restrictions at network level. With NACL's, you can also deny for ports which you do not want to allow access at all. |
KMS |
AWS Key Management Service (AWS KMS) is a managed service that you can use to create and control the encryption keys used to encrypt your data. You can use this directly in your applications or between AWS services that are integrated with KMS. |
Secrets Manager |
AWS provides this service where you can store all your secrets. The application can retrieve secrets with a call to Secrets Manager API to eliminate the need to hardcode sensitive information in configuration files or DB. |
Certificate Manager |
To establish secure network communication and identity of websites over the internet, AWS provides AWS certificate manager that you can use to create SSL/TLS certificates for your website. You can also import an outside certificate in the certificate manager. |
GuardDuty |
As the name suggests, AWS has developed an intelligent threat detection service using a machine learning technique which continuously monitors all the network and account level logs to check if there is any malicious activity happening and protect your AWS accounts and workloads. |
Inspector |
Inspector is a security assessment service that runs on your EC2 instances to identify if your application is exposed to vulnerabilities or deviates from best practices. For example, if your instances are exposed over the internet or any vulnerable software version is installed. |
Macie |
In AWS, all your flat file data is stored in S3. If you have any sensitive information in any of the buckets in S3, Macie can be used for that. Macie is another security service that used machine learning technique to discover, classify and protect sensitive information like PII data and reports to the user to take action against it. |
WAF & Shield |
WAF & Shield are services to avoid and block web attacks and exploits like DDOS, SQL Injection, Cross-site scripting etc. Before GO-LIVE, you can also enable IP based filtering so that the website can be accessed only from some specific IP's. |
Security Hub |
Security Hub provides you a consolidated dashboard for reports generated from Guardduty, Inspector and Macie. Sometimes it is troublesome to switch back and forth across different dashboard to identify threats and errors and there are chances we miss any service. Hence, this service helps you in provide one single view to get all reports with actionable graphs and tables. |
Config |
AWS Config keeps tracks of all the configuration changes you are making for all the resources in AWS. It keeps the record of current configurations and changes you are making on top of it and sends the details to SNS. You can review the changes and track the history of changes done to resources to identity any potential threat due to any misconfiguration. |
Cloudtrail |
AWS Cloudtrail records all the events happening to your account. Which user is logged-in, when he logged-in, what services he created, updated. Every detail is captured in AWS Cloudtrail. This service is used for audit purposes. |
VPC Flowlogs |
This service enabled you to capture information about IP traffic going to and from network interfaces into your VPC. It helps you to monitor the traffic that is coming to your instance. |
I would like to conclude this blog by stating that all the services mentioned above are aligned directly with the AWS Well-Architected Framework and thousands of customer success stories. When you understand the shared responsibility model and the value of each service, you are well on your way to demystifying security and building a better and secure platform on AWS Cloud.
Further Reading
25 AWS Security Tips: Securing Your AWS
The Fundamental Security Concepts in AWS - Part 1

