Security Architecture Review on a SASE Solution
Vendor security assessments can be very complex, especially when it comes to analyzing modern solutions. Obsolete threat modeling principles and frameworks become extremely unreliable and tricky as complexity increases. Security analysis also becomes further intricate as it is not limited to the application's inherent design but also how it is integrated with any organization's core network. Implementation and configuration induces vulnerabilities in the system if security is not a part of the development lifecycle. Recent trends suggest that organizations are now moving to SASE solutions, replacing existing vendors that provide services like CASB (Cloud access security broker), DLP (Data Loss Prevention), proxy solutions, etc.
What Is SASE?
Secure Access Service Edge (SASE) is a framework that provides network convergence alongside security services. It adds security to the ingress and egress network traffic. The technology stack usually comprises CASB, DLP, SWG (Secure Web Gateway), FWaaS (Firewall as a Service), NGFW (Network Firewall), SDN (Software Defined Networking), and ZTNA (Zero Trust Network Architecture) solutions.
Where Can We Utilize SASE Solutions?
1. Accessing Internet Securely: Organizations usually deploy proxy solutions at the user's workstation that direct HTTP and HTTPS traffic from endpoints to the internet. HTTPS traffic is decrypted at the proxy and processed through various security tools like DLP, IDS, etc. Note that some traffic passing through the proxy may include SSH and SFTP, which cannot be decrypted and are hence prone to threats. With a SASE solution in place, only traffic from approved sources is allowed. Also, the system has the capability to authenticate and inspect previously insecure protocols like SSH and SFTP.
2. Remote access and cloud access: Remote users can securely access internally, or cloud-hosted applications using features like remote secure connect. Moreover, SASE solutions can help replace CASB with the use of secure cloud access.
How and What To Review for a SASE Solution
Before any vendor is onboarded, it is very important to perform due diligence as a whole and architecturally review the application. One of the most effective review techniques that security architects follow is 'threat modeling.' There are multiple methods to create threat models, so implementations can vary by team. STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, DoS, Elevation of privilege), PASTA (Process for Attack Simulation and Threat Analysis), and VAST (Visual, Agile, and Simple Threat) are some of the common methodologies used.
Before a SASE solution can be considered, the first step is to understand the network. It is important to review an existing network diagram and understand changes to the data flow and the network itself.
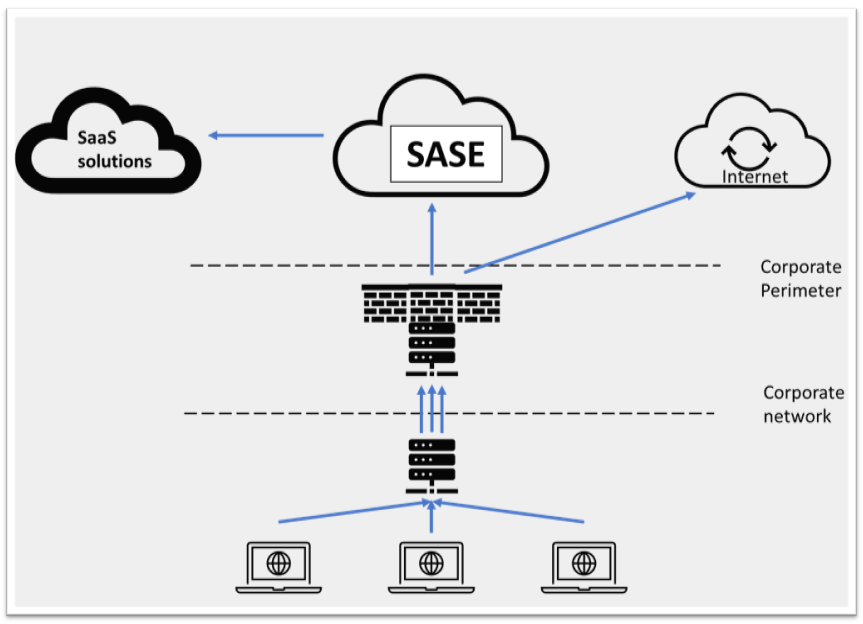
Once the network diagram is updated, start by identifying potential threats for each entity. Then create a list of controls and map them to the threats. You need to ensure that all concerns are addressed. SASE threat modeling may sound very complex but can be completed easily by breaking it up into smaller steps. Below is an example of using the STRIDE methodology for reference:
Entity 1: User
Spoofing:
- Threat: User's credentials are compromised and being used by a malicious actor to connect to the system.
- Control: Enable MFA.
Tampering:
- Threat: Brute force technique used to gain credentials.
- Control: Lock account after a specific number of failed attempts.
- Threat: Get access to the user's session.
- Control: Enable strong session management controls.
Repudiation:
- Threat: No proof of wrongdoing by the threat agent.
- Control: Log and archive user activity.
Information Disclosure:
- Threat: Information can be leaked from SASE hosting environment or through any connections going to and from SASE.
- Control: Only store the required user information; enable strong access and cryptographic controls; have a dedicated key for each tenant.
- Threat: Information can be leaked through connections going to and from SASE.
- Control: Use the secure protocol version, Block users or generate alerts for access over an insecure network.
Denial of Service:
- Threat: End user unable to access the service due to bandwidth or license issues.
- Control: Enable scalability feature for SASE endpoint systems.
Elevation of Privilege:
- Threat: User gains access to unauthorized data/service.
- Control: Set up RBAC (Role-based access control) for accessing internal applications.
- Threat: The user has illegal access.
- Control: Restrictive internet access.
Entity 2: User Connectivity to SASE
Spoofing:
- Threat: Accepting outside connection.
- Control: Verify the user before granting access.
Tampering:
- Threat: Man in the middle attack.
- Control: Use the most up-to-date and secure protocol versions for communication.
Repudiation:
- None
Information Disclosure:
- Threat: Network Sniffing or password is disclosed.
- Control: Use the most secure protocols.
- Threat: User or link redirect.
- Control: Restrict internet access, and use black-and-white listing of IPs, URLs, domains, and applications.
Denial of Service:
- Threat: Poor connectivity due to a large number of network hops.
- Control: Use a SASE provider with wider geographical coverage.
- Threat: Incompatible protocols used.
- Control: Use standard security protocols.
- Threat: Bandwidth issues.
- Control: Use bandwidth priority feature for critical applications.
Elevation of Privilege:
- None
Entity 3: Workstation
Spoofing:
- Threat: Fraudulent device used.
- Control: Add security controls to check device identity before connecting.
Tampering:
- Threat: Malware attack on workstation due to the user clicking on malicious links.
- Control: Enable malware analysis, inspect the files uploaded and isolate the browser on the SASE end.
- Threat: Direct connection bypassing SASE.
- Control: Monitor and restrict internet connections.
- Threat: Security control being disabled.
- Control: Allow only restricted user groups/admins to update user permissions.
Repudiation:
- Threat: Lack of evidence and tracking of the compromised system.
- Control: Log and monitor activity; generate alert in case of suspicion.
- Threat: Missing information on the malicious activity on the workstation.
- Control: Enable endpoint detection and response.
Information Disclosure:
- Threat: Leakage of sensitive information from the workstation.
- Control: Enable data loss prevention tools
Denial of Service:
- None
Elevation of Privilege:
- Threat: Workstation running with elevated privilege of SASE agent.
- Control: Restrict SASE agent's access; monitor privileged access closely.
Entity 4: SASE Service and Its Hosting Solution
Spoofing:
- Threat: Malicious endpoints hosted.
- Control: Establish trust before making connections.
- Threat: Admin account of SASE tenant and provider spoofed.
- Control: Use MFA for all admin connections.
Tampering:
- Threat: Vulnerabilities exploited, including zero-day attacks.
- Control: Periodic pen tests and vulnerability assessment, including patching activity, should be conducted.
- Threat: Data and config modification.
- Control: Controlled change management procedure; enable RBAC with close monitoring for admin.
- Threat: Unauthorized physical access to data centers.
- Control: Enable badging and other physical security controls.
Repudiation:
- Threat: Configuration changes could not be tracked or monitored.
- Control: Centralize SIEM solution and enforce strict change management policies.
- Threat: Could not identify the cause of unexpected issues.
- Control: Enforce enterprise-level monitoring and alerting.
Information Disclosure:
- Threat: Data compromised and shared by a third party.
- Control: NDAs should be signed, and strong access management policies should be in place.
- Threat: Data not encrypted on hard drives and archives; data exposed in case of any required investigations.
- Control: Encrypt data at rest; tokenize and mask, if required.
Denial of Service:
- Threat: Application not available due to network or application level Denial of Service attack.
- Control: Use WAF and CDN for DDoS prevention.
Elevation of Privilege:
- Threat: Insider threat due to the SASE platform being compromised.
- Control: Set up the SASE application within the demilitarized zones (DMZs) and restrict the ingress traffic.
- Control: Set up the SASE application within the demilitarized zones (DMZs) and restrict the ingress traffic.
Entity 5: Application/Internal Connections Through SASE
Spoofing:
- Threat: SASE source spoofed.
- Control: Use mutual authentication techniques.
Tampering:
- Threat: MiTM attack.
- Control: Use only secure protocol versions.
- Threat: Malicious data through the tunnel between SASE and data hosting environment.
- Control: Strong session management controls.
Repudiation:
- Threat: Connections not being monitored.
- Control: Log every request to and from the SASE to target application
Information Disclosure:
- Threat: Network Sniffing attack and password leakage
- Control: Access management and redirect traffic through private tunnels, Always use the latest and secure version of protocols
- Threat: Data leaked through the tunnel between SASE and the data hosting environment.
- Control: DLP and content inspection for the information flowing through the tunnel.
Denial of Service:
- Threat: Broken network connection between the data center and SASE.
- Control: Multiple, alternative and reliable paths are created within the network.
Elevation of Privilege:
- Threat: One tenant accessing system through other tenant's system/credentials.
- Control: RBAC; Each connection between tenants should be uniquely identifiable and can be controlled
SASE solutions can be very useful to an organization, both from a security and business perspective. However, it is essential to understand where the data is hosted, who can access it, which controls are in place at the hosting location, and how the connectivity is made reliable and secure. Having a single solution helps teams centralize management and enable better coordination for various operational tasks. Industries advocate the use of SASE solutions, but it is important that implementation and operational risks are reviewed before onboarding the tool.

